Illustrate why!
We will cover several methods for circumventing network
restrictions.
For example, you may want to use BitTorrent to download an open source
Linux.iso file.
These location-obfuscation methods themselves are all perfectly legal in
the USA and most of Western Europe.
This is not true in some counties, e.g., China, Russia (where obscuring
your IP address is now illegal).
What is a Proxy?
https://en.wikipedia.org/wiki/Proxy_server
What is a VPN?
It’s a more general technology, which can be used for a sub-purpose
here: a very thin layer of security.
https://en.wikipedia.org/wiki/Virtual_private_network
There are numerous VPN implementations:
Technologies to set up VPNs are variable:
IPSec (i.e., IPv6 default encryption, good)
Wireguard (fast, supposedly nice)
https://www.wireguard.com/
https://en.wikipedia.org/wiki/WireGuard
OpenVPN (standard, open-source)
https://openvpn.net/
https://en.wikipedia.org/wiki/OpenVPN
https://openvpn.net/community-resources/openvpn-cryptographic-layer/
(encryption through UDP)
https://openvpn.net/community-resources/hardening-openvpn-security/
Some other decent options, and a bunch of other proprietary trash
A VPN for privacy requires that you trust the VPN provider, a tall
order in many cases…
Many of these hyped-up services have you install their own questionable
software.
In general, just finding a free one that can use openVPN or Wireguard is
a decent way to go:
https://duckduckgo.com/?q=free+openvpn&ia=web
This is one of the less suspicious ones, and there are others (this is
not an endorsement):
https://mullvad.net/en
I actually think paying for VPNs tend to NOT be worth it,
unless you’re paying for a fast way to pirate data with moderate
security.
Can be done either in your host or VM, whichever you prefer.
Determine what websites view your IP address to be.
Open Choose a Linux ISO (or other legal file) that offers a BitTorrent
download option.
Start up Wireshark, observe the protocol details whet attempting to
download.
On campus it may not work/download.
In Wireshark, click the “analyze” menu, then “enabled protocols”,
search for torrent, then turn on (check) all the BitTorrent related
check boxes.
Does traffic show up as UDP/uTP/TCP?
Do you see any BitTorrent related traffic?
If so, what does it look like?
Choose a VPN (Setup varies by choice).
You can google free OpenVPN VPNs, e.g.,
https://www.freeopenvpn.org
https://www.vpngate.net/EN/
On whatever platform you want (VM or host) setup a VPN.
sudo openvpn --config <config_file_you_download>.ovpnDoes your VPN tunnel through UDP or TCP?
Does it support UDP traffic?
After setting up that VPN/proxy, verify that your IP address no longer
displays as your own ISP’s.
Then, perform the same Wireshark BitTorrent observation activity as
above again.
Did what you observe change?
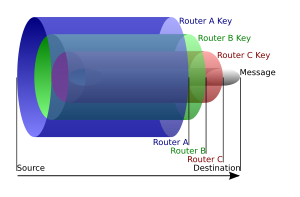
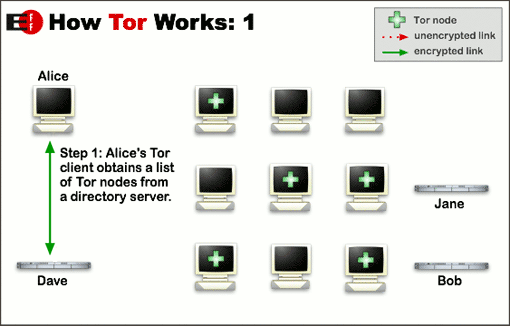
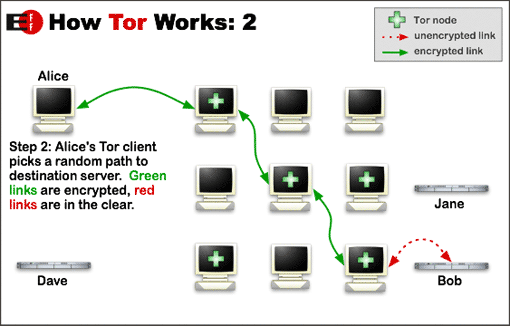
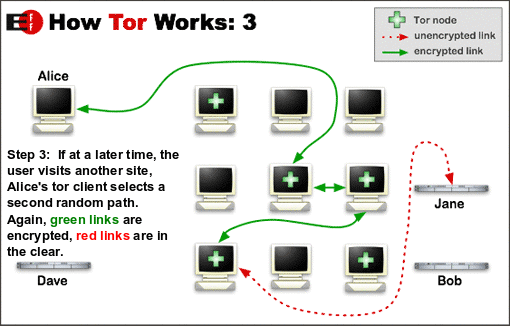
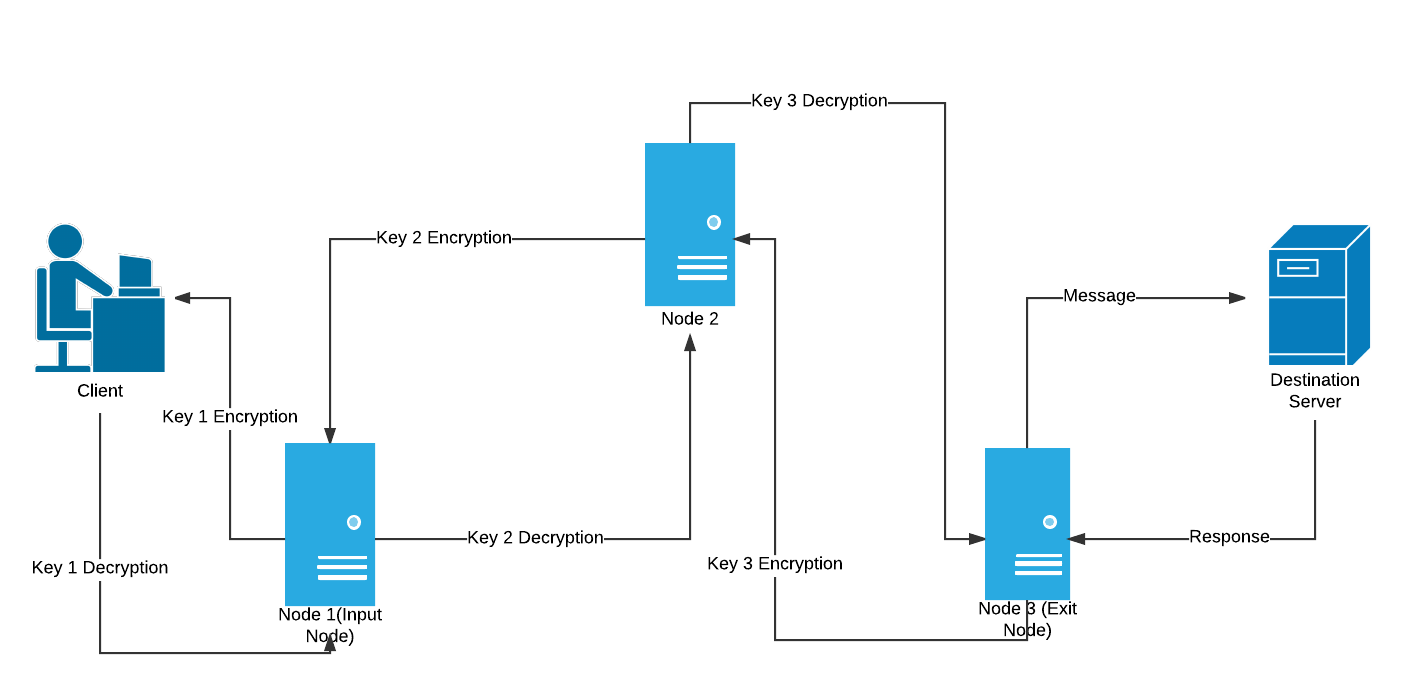
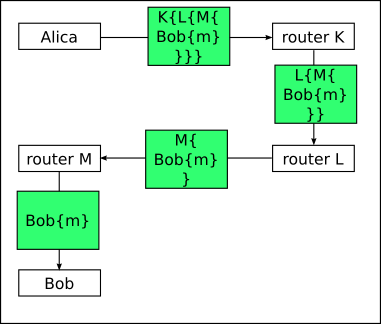
What is Tor?
https://www.eff.org/pages/tor-and-https
(infographic)
https://2019.www.torproject.org/about/overview.html.en
https://en.wikipedia.org/wiki/Onion_routing
https://www.geeksforgeeks.org/onion-routing/
The important concept below is that neighbors more than one away
can’t know further away neighbors.
Illustrate why!






Technical details
https://gitweb.torproject.org/torspec.git/tree/tor-spec.txt
https://svn.torproject.org/svn/projects/design-paper/blocking.html
Note:
Whonix can be securely used to host an arbitrary web-service (e.g.,
website),
from WHEREVER you can actually connect to the internet!
Can be done either in your host or VM, whichever you prefer.
Using normal internet, determine what websites verify your IP address to
be.
Download the Tor Browser
What do websites think your IP address is from within the Tor
browser?
Where is it?
Start up Wireshark, what does your traffic look like when browsing
now?
Edit your torrc file, to make sure you have a US-only exit IP, verify it
works.
What was the IP?
What US state did you end in?
Edit your torrc file, to make sure you have a DE (Germany) exit IP,
verify it works.
What was the IP?
Open Tor browser proxy settings
Firefox proxy settings
Change your regular browsers settings to those of the Tor
browsers.
Confirm that your new browser is also routed through Tor,
by checking that your regular browser has a tor IP:
https://check.torproject.org/
Read the Whonix documentation above, and here: https://www.whonix.org/wiki/Other_Operating_Systems
Create a Whonix gateway VM and a Whonix Workstation VM (this is more
secure than the TBB)
Observe the VirtualBox and Whonix Workstation Guest IP
configuration
(via graphical networkmanager in the top left menu).
Using those settings of the Whonix workstation, mimic them for one of
your other Linux (or Windows) VMs.
You will need to set a static IP to the new custom workstation (link
above shows IP details).
Confirm that in the other guest VM that all your traffic routes through
tor.
Can applications in this VM escape directly to the regular
internet?
Can this kind of gateway apply to any proxy, or just Tor?
That is, can you have a forceful gateyway for other proxies.
What is I2P?
A full overlay layer, not just exit node,
for anonymizing IP addresses of virtually any service you like.
How does it compare to Tor?
https://geti2p.net/en/comparison/tor
It uses Garlic rather than Onion routing:
https://en.wikipedia.org/wiki/Garlic_routing
https://geti2p.net/en/docs/how/garlic-routing
https://geti2p.net/en/docs/how/intro
Show SSU discussion here (like uTP):
https://geti2p.net/en/docs/how/tech-intro
https://geti2p.net/en/docs/applications/supported
https://en.wikipedia.org/wiki/I2P#Software
Access on I2P itself:
https://thetinhat.i2p/tutorials/darknets/i2p.html
Do you just want to download Linux.iso and bypass restrictions?
A VPN is sufficient.
Do you Want better security, robustness, or privacy for
torrenting?
https://en.wikipedia.org/wiki/I2P#File_sharing
https://geti2p.net/en/docs/applications/bittorrent
https://thetinhat.com/tutorials/darknets/torrent-anonymously-i2p-vpn-free.html
https://thetinhat.com/tutorials/darknets/i2p.html
An interesting client:
https://en.wikipedia.org/wiki/Vuze#Bridging_between_I2P_and_the_clearnet
And the open source fork:
https://www.biglybt.com/features.php
I2P can be also used to host an arbitrary web-service (e.g.,
website),
from WHEREVER you can actually connect to the internet.
Install I2P.
Start the “router”.
Configure your browser’s proxy to view eepsites.
Start up Wireshark.
Navigate to: http://secure.thetinhat.i2p/
What is the base32.i2p address of thetinhat?
Get this from the router console, directory, where you can search;
it’s a form of local distributed DNS.
What protocol is I2P being run over?
What does the traffic look like in Wireshark?
Notice the BitTorrent client.
Use it if you want.
Hint: visit the postman’s index,
linked in the BitTorrent client configuration settings.
https://www.privacytools.io/anonymizing-networks
https://prism-break.org/en/all/#anonymizing-networks
Easy Tor hidden service hosting:
https://onionshare.org/
Demo assignment