
Random side note:
Many
Vim users (and others) just remap Caps-lock to
Ctrl…Mine is actually a mouse overlay layer.
Previous: 00-Inspiration.html

Random side note:
Many Vim users (and others) just remap Caps-lock to
Ctrl…
Mine is actually a mouse overlay layer.
Show these in class:
https://en.wikipedia.org/wiki/Information_security
https://en.wikipedia.org/wiki/Timeline_of_computer_security_hacker_history
https://www.informationisbeautiful.net/visualizations/worlds-biggest-data-breaches-hacks/
document.querySelector('video').playbackRate = 1.2Which impacted cyber-physical infrastructure, hospitals, etc.
Overview: Ransomware cryptoworm targeted computers running Microsoft Windows OS by encrypting data and demanding ransom payments in Bitcoin. Those still running older, unsupported versions of Microsoft Windows, such as Windows XP and Windows Server 2003, were initially at particular risk. May 12, 2017, UK’s National Health Service was affected.
Exploit: WannaCry propagates using EternalBlue, an exploit of Windows’ Server Message Block (SMB) protocol. Much of the attention and comment around the event was occasioned by the fact that the U.S. National Security Agency (NSA) had already discovered the vulnerability, but used it to create an exploit for its own offensive work, rather than report it to Microsoft. The vulnerability exists because the SMB version 1 (SMBv1) server in various versions of Microsoft Windows mishandles specially crafted packets from remote attackers, allowing them to execute arbitrary code on the target computer.
President and Chief Legal Officer (CLO) of Microsoft in an official
public statement announced, quote:
“This attack provides yet another example of why the stockpiling
of vulnerabilities by governments is such a problem.”
https://blogs.microsoft.com/on-the-issues/2017/05/14/need-urgent-collective-action-keep-people-safe-online-lessons-last-weeks-cyberattack/
How to protect cyber-physical infrastructure?
The NIST Computer Security Handbook defines the term Computer Security as:
“The protection afforded to an automated information system,
in order to attain the applicable objectives of preserving the
integrity, availability, and
confidentiality of information system resources”,
including hardware, software, firmware, information/data, and
telecommunications
Confidentiality:
Preserving authorized restrictions on information access and
disclosure,
including means for protecting personal privacy and proprietary
information
Integrity:
Guarding against improper information modification or destruction,
including ensuring information non-repudiation and authenticity
Availability:
Ensuring timely and reliable access to and use of information
Authenticity:
is sometimes included,
as the property of being genuine, verifiable, and trusted.
CIA triad applied
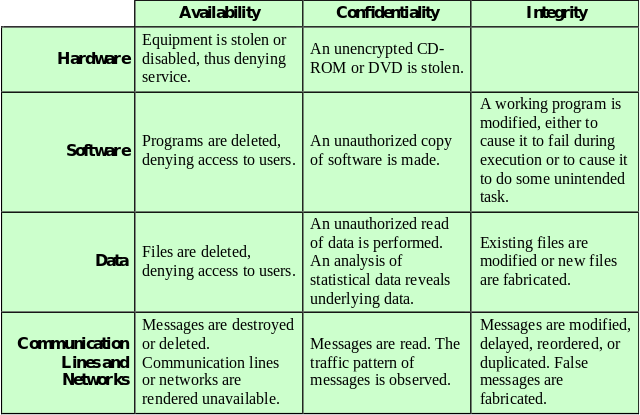
Hardware integrity is a growing area of concern (empty box above).
Ex: Supply chain compromise.
Discuss/Ask: What else could result in this?
I would tell you an information security joke…
But it’s confidential.
Computer security is not simple!
Security is simultaneously one of the most and least formal
disciplines in computation.
e.g., human factors versus cryptography
Many algorithms, protocols, operating systems, technical layers, and parties may be involved.
Attackers only need to find a single weakness,
but the developer needs to find all weaknesses.
Why? Mobility matters:
Model a national lab that can’t keep it’s resources mobile?
Model a person who can move around?
Users and system managers tend to not see the benefits of security
until a failure occurs.
Security is often an afterthought,
in being incorporated into a system,
after the design is complete.
Security is thought of as an impediment to efficient and user-friendly
operation.
Does it have to be?
Arms race requires regular and constant monitoring.
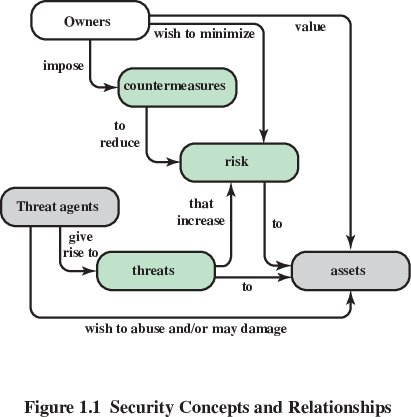
In class, ponder and define each element in this diagram.
For any given piece of information you may want to protect,
each party who might access or manipulate that information must be
considered,
along with that party’s capabilities, motivations, consequences,
and
probabilities of mechanisms of compromise.
Imagine being you, protecting your web
traffic,
considering mechanisms of compromise,
for various parties with varying degrees of access,
and varying motivations:
Assets (and their relative values):
Threat agents (with associated probabilities):
Threat mechanisms (with associated probabilities, costs):
Countermeasures (with associated probabilities of being effictive and costs):
Risk/Consequences (with associated probabilities and costs)
Diagram all of these into a network like above.
Do all countermeasures work against all threat agents?
In a perfect world, you protect everything with all
countermeasures.
Now, given your limited time and resources,
how to balance the costs and probabilities?
How does this differ depending on where you are browsing from?
Imagine being an engineer who works on power grid infrastructure operations designs and schedules?
Discuss/Ask:
Assets (and their relative values):
* ?
Threat agents (with associated probabilities):
* ?
Threat mechanisms (with associated probabilities and costs):
* ?
Countermeasures (with associated probabilities of being effictive and
costs):
* ?
Risk/Consequences (with associated probabilities and costs)
* ?
Note:
This kind of threat modeling is one thing the non-free Pfleeger book
really emphasizes well.
+++++++++++++++++++++
Cahoot-01.1
Hardware: storage, processing, and
communications
Software: OS, system utilities, applications
Data: files, databases, password databases
Communication facilities and networks: LAN, WAN,
bridges, routers, etc
Discuss/Ask:
Any other assets we missed?
What are all the inputs to computers?
lead to several categories of fault:
Corrupted (loss of integrity): wrong answers
Leaky (loss of confidentiality): information leaks
Unavailable or very slow (loss of availability): server down
(potential):
Capable of exploiting vulnerabilities
Represent potential security harm to an asset
(threats carried out):
Passive – attempt to learn or make use of
information from the system that does not affect system resources
Active – attempt to alter system resources or affect
their operation
Insider – initiated by an entity inside the security
parameter
Outsider – initiated from outside the perimeter
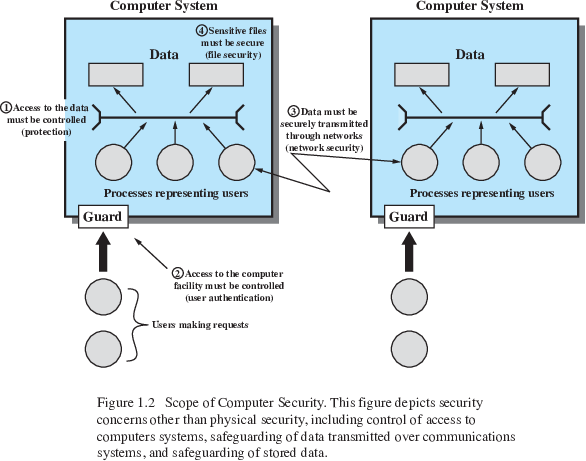
Slowly ponder the parts of this in class:
Actually review these:
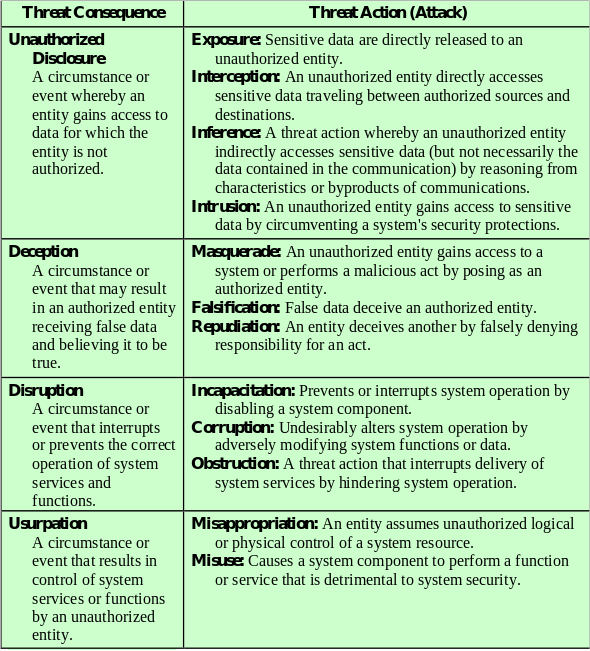
Attempt to learn or make use of information from the system,
but does not affect system resources.
Eavesdrop on, or monitor transmissions.
Goal of attacker is to obtain information that is being transmitted.
Two categories:
Attempt to alter system resources or affect their operation.
Involve some modification of the data stream or the creation of a false
stream.
Four categories:
Replay: involves the passive capture of a data unit and its subsequent re-transmission to produce an unauthorized effect.
Masquerade: one entity pretends to be a different entity. For example, authentication sequences can be captured and replayed after a valid authentication sequence has taken place
Modification of messages: some portion of a legitimate message is altered, or that messages are delayed or reordered, to produce an unauthorized effect.
Denial of service: prevents or inhibits the normal use or management of communication
+++++++++++++++++++++
Cahoot-01.2
Can we think of examples of each?
Discuss/ask?
What about security via obscurity?
Reachable and exploitable vulnerabilities in a system.
Examples are:
Discuss/ask:
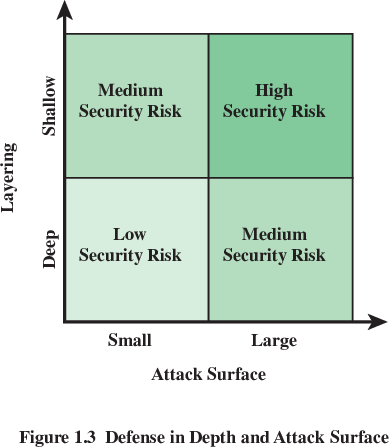
What are the two biggest attack surfaces for:
Network Attack Surface
Software Attack Surface
Human Attack Surface
Browser Attack Surface
+++++++++++++++++++++
Cahoot-01.3
Another method of modeling threats and exploits/attacks
Attack tree for internet banking
Green: attack;
UT/U: user equipment;
CC: communication links;
IBS: Internet Banking Server;
White: category of attack
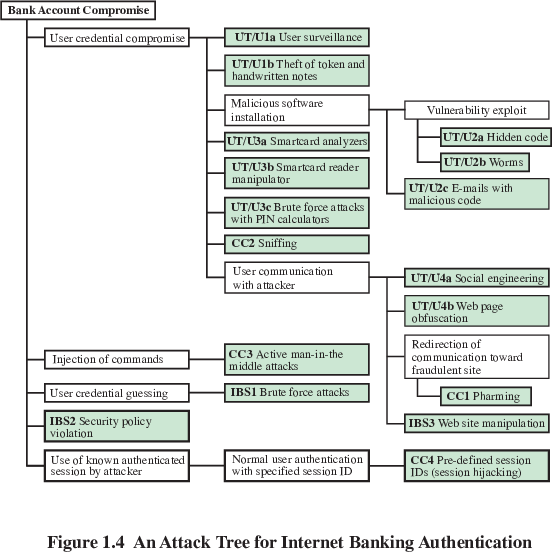
Discuss/Ask:
Attack tree for the following?
Side-note:
what is actually written in FERPA/HIPPA?
Within an organization/institution:
Security Policy:
Formal statement of rules and practices that specify or regulate how a
system or organization provides security services to protect sensitive
and critical system resources
Assurance/Trust:
The degree of confidence one has that the security measures, both
technical and operational, work as intended to protect the system and
the information it processes
Discuss/Ask:
Is this form of trust formal, statistical, provable, or subjective?
Both?
Evaluation:
Process of examining a computer product or system with respect to
certain criteria
Discuss/Ask:
Is this formal, statistical, provable, or subjective? Both?
Security Implementation:
Involves four complementary courses of action:
All security is ultimately either cryptographic or physical
(including threats of physical),
BUT there is a messy landscape of technical and practical
considerations.
Using physical and cryptographic considerations,
design of accessible software interfaces
(often remote, or protected from physical access) is also critical.
Read the first chapter of the cryptography book!