
Previous: 19a-AccessControls.html

document.querySelector('video').playbackRate = 1.2#!/bin/bash
### Man files
# General: these are the same
man chmod
man 1 chmod
# When you see this --> "see also: chmod(2)" do this:
man 2 chmod
### help
chmod --help
### info (does not have the same 'less' shortcuts
info chmod
### To search type / then your term, then enter,
# then n or shift-n to search forward and backward!Search for term
/term enter
Next term
n
Previous term
shift n
http://catcode.com/teachmod/
https://en.wikipedia.org/wiki/File_system_permissions#Traditional_Unix_permissions
https://en.wikipedia.org/wiki/Chmod
https://en.wikipedia.org/wiki/Modes_(Unix)
http://labor-liber.org/en/gnu-linux/introduction/
(p69-77)
Show this in lecture:
http://permissions-calculator.org/
https://file-permissions.ninja
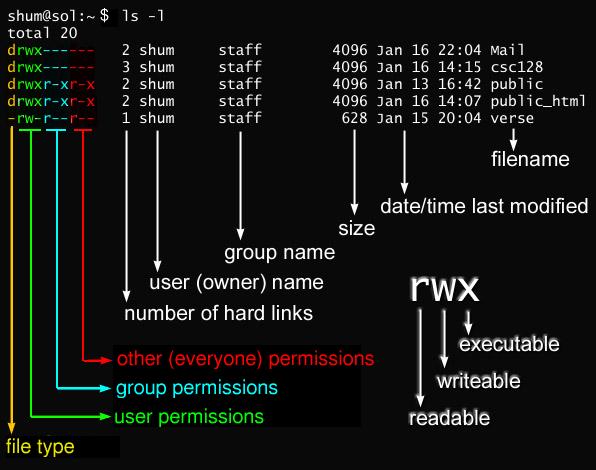
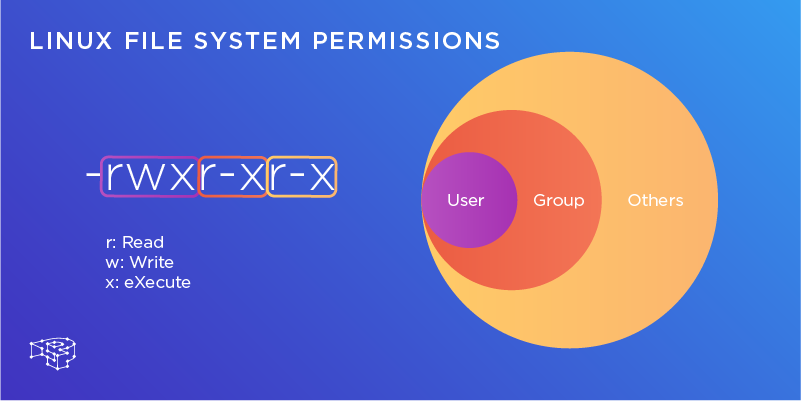
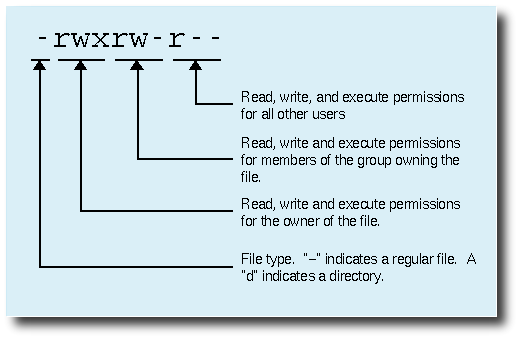
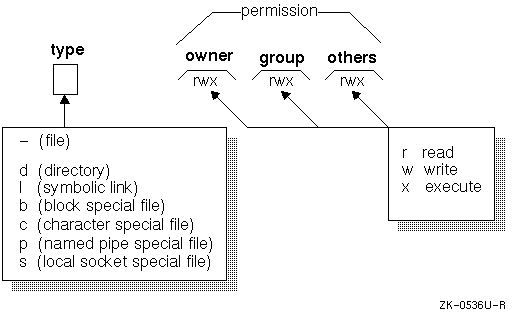
Show some example permissions
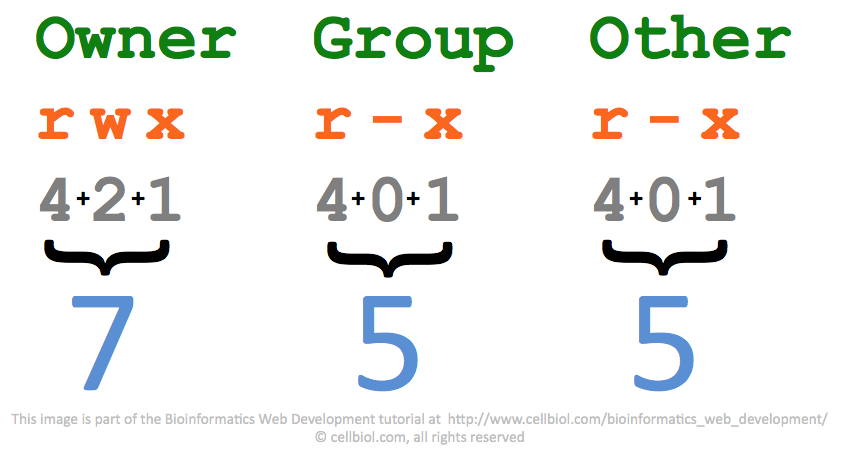
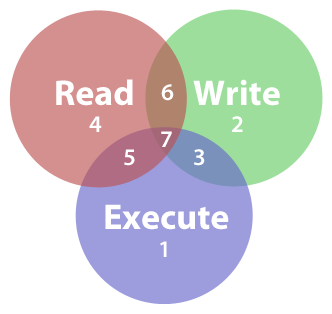
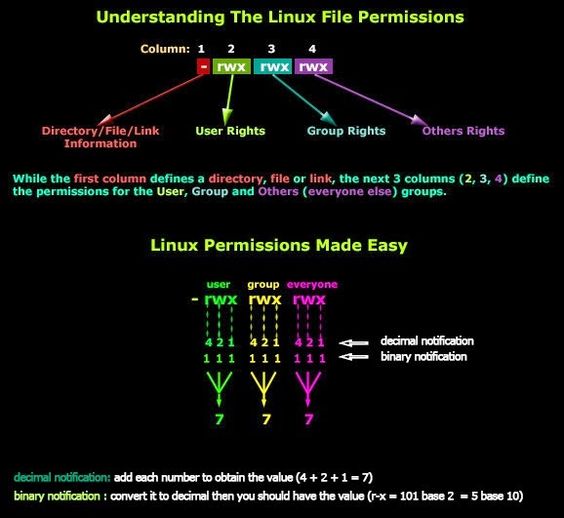
The symbolic form is easier, better human factors
(safer),
and less likely to be screwed up than the numeric
form;
use the symbolic form preferably.

+++++++++++++++++++++
Cahoot-19b.1
#!/bin/bash
ls -l
touch file.txt
ls -l
stat file.txt
ls -i file.txt
# Basic DAC
whatis chmod
which chmod
man chmod
chmod --help
# Though numeric permissions (e.g., chmod 777 file.txt) work fine,
# the following syntax is much better:
chmod u=rw file.txt
chmod u+x file.txt
touch file2.txt
chmod o+rw,g+rw file2.txt
chmod go-rwx file2.txt
# Executable +x
echo '#!/usr/bin/python3' >script.py
echo "print('hi')" >>script.py
./script.py
chmod +x script.py
./script.py
# For setting directories as accessible
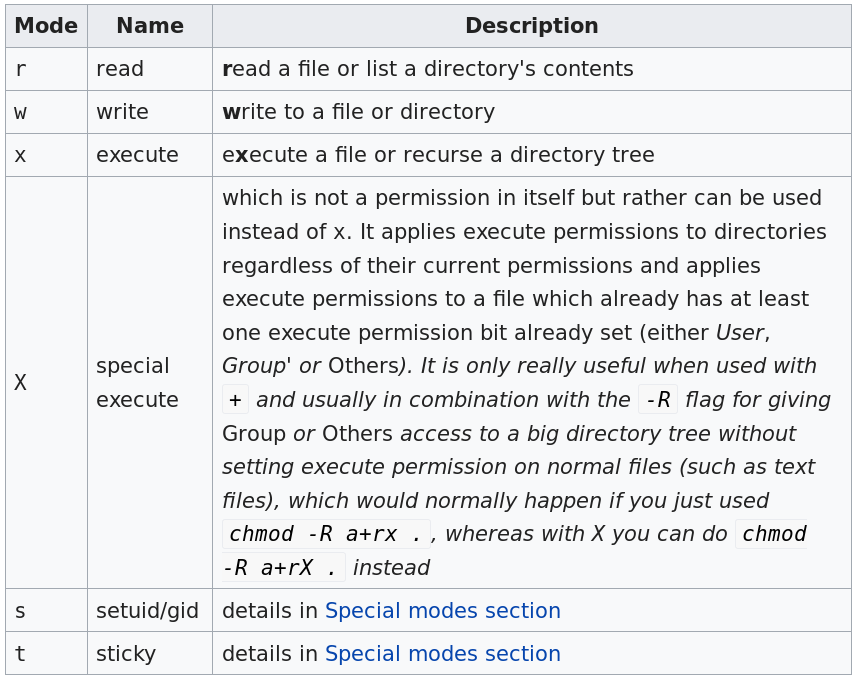
# Note: difference between +x and +X
chmod --recursive u+X directiory/subdirectory
# What about the permissions of the shadow file
sudo stat /etc/shadow
sudo ls -l /etc/shadow
# What about the permissions of the passwd file
sudo stat /etc/passwd
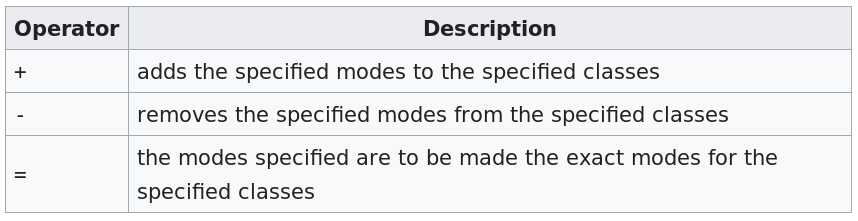
sudo ls -l /etc/passwdEach symbolic chmod command has 3 parts:
https://en.wikipedia.org/wiki/Chmod#Special_modes
http://labor-liber.org/en/gnu-linux/introduction/index.php?diapo=special_permissions
(good!)
https://docs.oracle.com/cd/E19683-01/816-4883/secfile-69/index.html
https://www.thegeekdiary.com/linux-interview-questions-special-permissions-suid-sgid-and-sticky-bit/
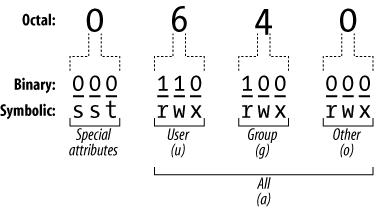
Special permissions on files and directories:
| Special perm | On file | On dir |
|---|---|---|
| SGID or Set Group ID | The effective group of an executing program is the file owner group. | Files created in the directory inherit its GID. |
| SUID or Set User ID | A program is executed with the file owner’s permissions (rather than with the permissions of the user who executes it). | Files created in the directory inherit its UID. |
| Sticky (bit) | A program sticks in memory after execution (old, system dependent) | Any user can create files, but only the owner of a file can delete it. |
Permissions as output in columns 2 to 10 of ls -l and their meaning.
**Permissions** **Meaning**
--S------ SUID is set, but user (owner) execute is not set.
--s------ SUID and user execute are both set.
-----S--- SGID is set, but group execute is not set.
-----s--- SGID and group execute are both set.
--------T Sticky bit is set, bot other execute is not set.
--------t Sticky bit and other execute are both set.https://en.wikipedia.org/wiki/Setuid
This is the binary executable program for changing your password,
not the file where your password is actually stored.
#!/bin/bash
# setuid bit will show as s in execute place
which passwd
sudo ls -l /usr/bin/passwd
sudo stat /usr/bin/passwdThe impact of this special bit is that:
the user can change their own password,
by effectively executing this program as root!
Discussion question:
Occasionally binaries have vulnerabilites
What happens if /usr/bin/passwd has a bug or
vulnerability?
What happens if that vulnerability enables a shell?
Why is the SUID bit relevant in this situation?
How to find files with SUID or SGID
bits set?
Discussion question:
Why might you want to do this?
The list of files this produces is interesting!
These binaries need to be well-tested!
#!/bin/bash
# find / -perm +mode has been deprecated
# To find all the files with SUID but set, use the below command
sudo find / -perm -u=s
sudo find / -perm /u=s
# To find all the files with SGID bit set, use the below command
sudo find / -perm -g=s
sudo find / -perm /g=shttps://en.wikipedia.org/wiki/Sticky_bit
The sticky bit works in a different way than it used to.
It no longer has no effect on files.
When used on a directory,
all the files in said directory,
will be modifiable only by their owners.
A typical case in which it is used,
involves the /tmp/ directory.
/tmp/ is writable by all users on the system.
Thus, to make impossible for one user to delete the files of another
one,
the sticky bit is set:
#!/bin/bash
# Sticky bit will show as t in the execute place
ll /
# see /tmp folder
ls -ld /tmp
stat /tmp
# Sticky can be set by:
chmod u+s /path/to/file.txt
chmod g+s /path/to/file.txthttps://en.wikipedia.org/wiki/Umask
Like with basic permissions, symbolic is easier/better:
https://en.wikipedia.org/wiki/Umask#Setting_the_mask_using_symbolic_notation
On most Linux/Unix/BSD systems, defaults are:
Files
666 (rw- rw- rw-)
Dirs
777 (rwx rwx rwx)
This default is modified using the
umask command.
For example, 0002, prescribes that other
(o) can’t write:
0002
u=rwx, g=rwx, o=rxWhy?
The logic is that we apply it by subtracting the umask,
though the numeric form is best thought about in binary:
666-002 = 664 (rw- rw- r--)
110 110 110
- 000 000 010
________________
110 110 100
777-002 = 775 (rwx rwx r-x)
111 111 111
- 000 000 010
________________
111 111 101**Octal digit Permissions the mask will prohibit from being set during file creation**
0 any permission may be set (read, write, execute)
1 setting of execute permission is prohibited (read and write)
2 setting of write permission is prohibited (read and execute)
3 setting of write and execute permission is prohibited (read only)
4 setting of read permission is prohibited (write and execute)
5 setting of read and execute permission is prohibited (write only)
6 setting of read and write permission is prohibited (execute only)
7 all permissions are prohibited from being set (no permissions)The default mask is applied whenever a file is created.
If the mask has a bit set to “1”,
that means the corresponding file permission will always be
disabled,
when files are subsequently created.
A bit set to “0” in the mask means that:
the corresponding permission will be determined by both,
the requesting process and the OS,
when files are subsequently created.
In other words, the mask acts as a last-stage filter,
that strips away permissions as a file is created
Each bit that is set to a “1”,
strips away that corresponding permission for the file.
chmod -R g=,o= .#!/bin/bash
# To create secure defaults on file creation:
whatis umask
which umask
man umask
umask --help
info umask
# numeric
umask
# symbolic
umask -S
# For example, to tighten on a single user system,
# you could remove all from group and other,
# by running this on shell init,
# for example in ~/.bash_profile or /home/user/.config/fish/config.fish
umask u=rwx,g-rwx,o-rwx
# or
umask u=rwx,g=,o=
# or more simply
umask go=
umask -S
umask
# This would set the mask so that it would:
# prohibit the write permission from being set for the user,
# while leaving the rest of the flags unchanged;
# allow the read permission to be enabled for the group,
# while prohibiting write and execute permission for the group;
# allow the read permission to be enabled for others,
# while leaving the rest of the other flags unchanged.
umask u-w,g=r,o+r
# If you want to clean up an existing /home/user directory,
# where files were created with a more lax umask:
chmod -R g=,o= .
chmod -R g,o= .
chmod -R g-rwx,o-rwx .To see a nicely formatted list of the attributes:
https://en.wikipedia.org/wiki/Chattr
To stop a file from being modified by anyone, or force the OS to do secure deletion on a particular file:
#!/bin/bash
# Other file attributes
whatis chattr
which chattr
man chattr
info chattr
chattr --help
# can't be changed
touch immutablefile.txt
sudo chattr +i immutablefile.txt
# Can't modify
vim immutablefile.txt
rm immutablefile.txt
sudo chattr -i immutablefile.txt
rm immutablefile.txt
# Securely deleted when deleted
touch extraspecialsecuretempfile.txt
chattr +s extraspecialsecuretempfile.txt
# This may or may not be respected by your ssd hard drive itself.
# Just encrypt anyway.https://en.wikipedia.org/wiki/Access_control_list
(not a Linux specific page)
https://www.computerhope.com/unix/ugetfacl.htm
getfacl and setfacl enable manipulating
more advanced access control lists.
If additional ACL are used via getfactl and
setfacl,
then a ‘+’ will appear after the permissions.
#!/bin/bash
touch file1.txt
touch file2.txt
# add a user (more to come on next page)
sudo useradd bob
sudo passwd bob
# User ownership changes
whatis chown
which chown
man chown
chown --help
sudo chown bob file1.txt
ls -l # note bob now owns file
##### ACL
# More advanced ACL than basic DAC
whatis getfacl
which getfacl
man getfacl
getfacl --help
getfacl file1.txt
whatis setfacl
which setfacl
man setfacl
setfacl --help
# to add another user or group to a file using ACL
# (rather than a class group or ACL group).
setfacl -m u:userlisa:r file1.txt
setfacl -m g:mygroup:rw file1.txt
getfacl file1.txt
getfacl file2.txt
whatis chacl
man chacl
chacl --helpIf SELinux permissions are used,
then you may see a ‘.’ after the permissions.
ls -Z
lists them
#!/bin/bash
# Arbitrarily more advanced ABAC (full lecture coming up later)
ls -Z # for selinux permissionsMore on SELinux to come in a later lecture: 21c-AppArmorSELinux.html
+++++++++++++++++++++
Cahoot-19b.2