If you don’t get why this contrast is funny,
search for a video of the artist and the last line of the first paragraph.
I clearly can’t show it in class…

If you don’t get why this contrast is funny,
search for a video of the artist and the last line of the first
paragraph.
I clearly can’t show it in class…
Chapter 6 and 7, Block and Stream Ciphers:
https://github.com/crypto101/crypto101.github.io/raw/master/Crypto101.pdf
Also referred to as: Conventional, Secret-key, or Single-key
encryption
It was the only alternative, before public-key encryption in
1970’s
It is still the most widely used scheme.
Basics:
1. Plaintext
2. Encryption algorithm
3. Secret key
4. Ciphertext
5. Decryption algorithm
Substitution - each element in the plaintext is mapped into another element
Transposition - elements in plaintext are rearranged
Block cipher - processes input one block of elements
at a time
https://en.wikipedia.org/wiki/Block_cipher
Stream cipher - processes the input elements
continuously
https://en.wikipedia.org/wiki/Stream_cipher
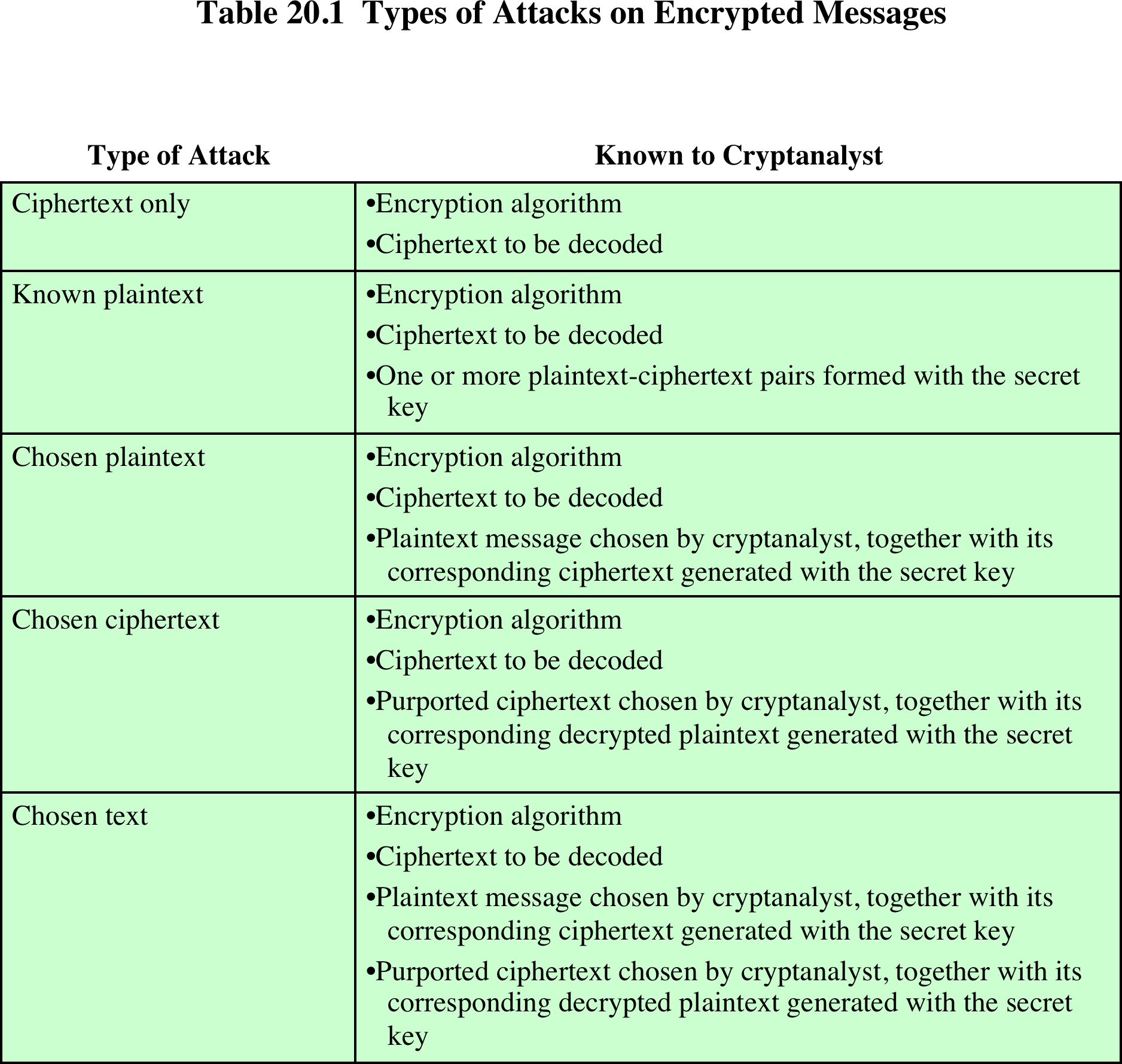
Attacks come in a variety of academic and/or realistic flavors:
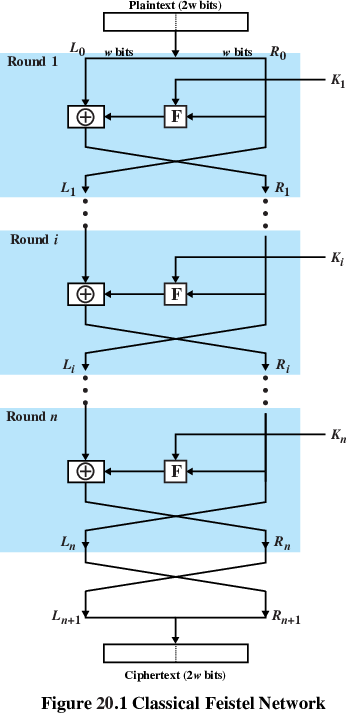
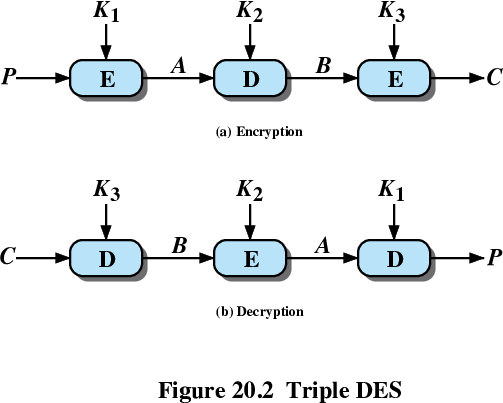
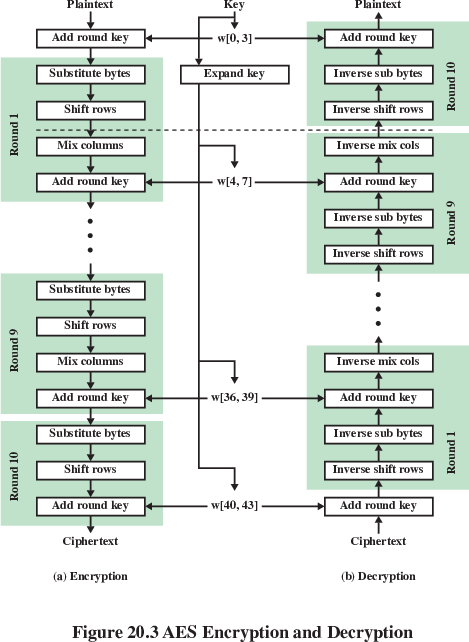
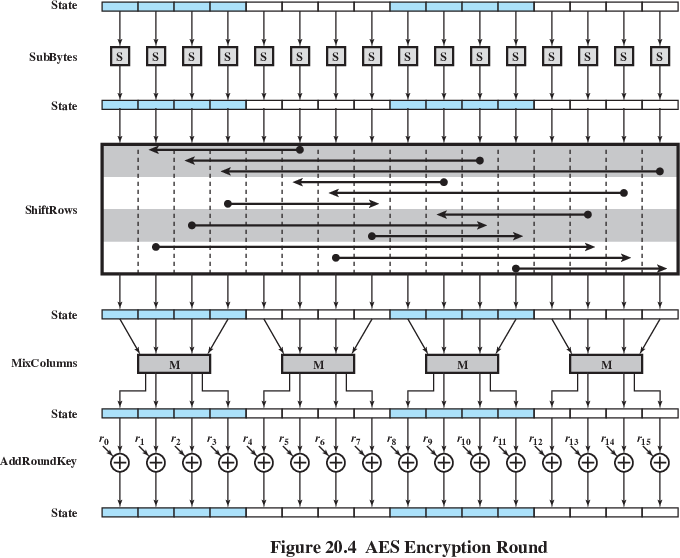
AES Encryption Round
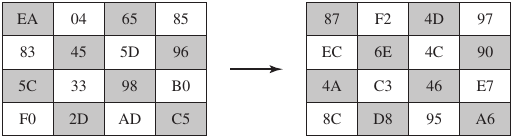
Replace according to these lookup tables:
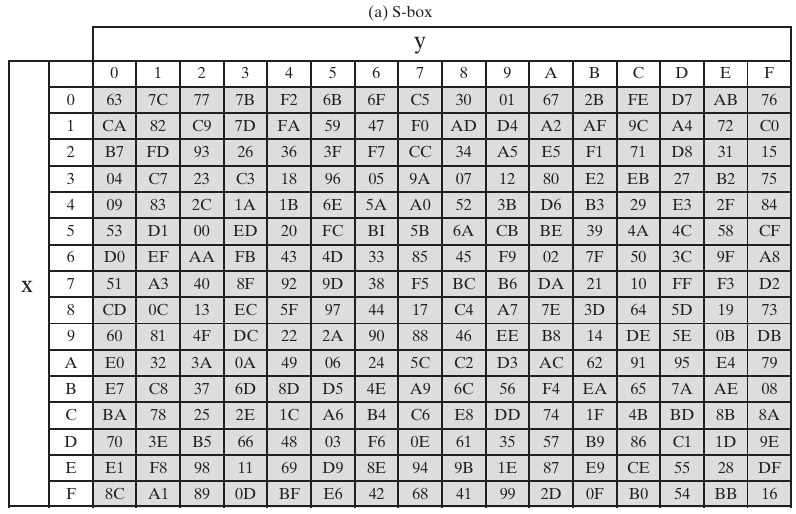
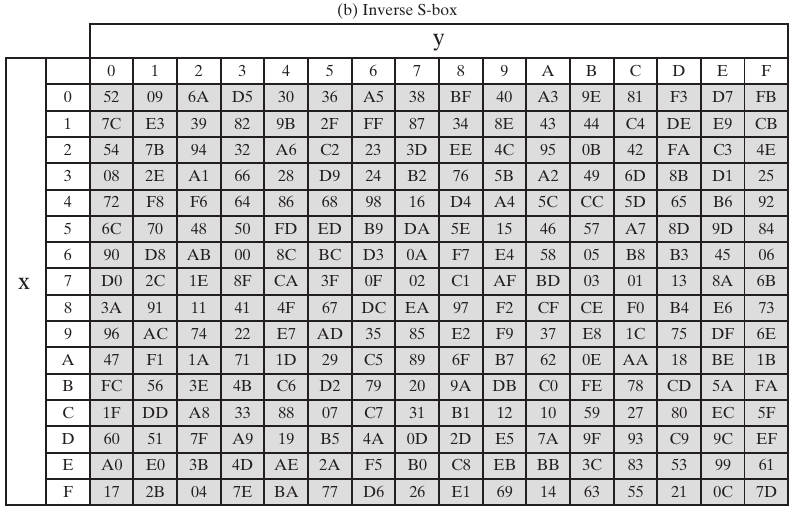
Note: how are these tables created?
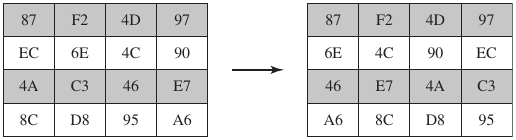
Spin the “padlock” of the rows, by increasing numbers of clicks.
To move individual bytes from one column to another and spread bytes
over columns.
On encryption left rotate each row of State by 0, 1, 2, 3 bytes
respectively.
Decryption does reverse.
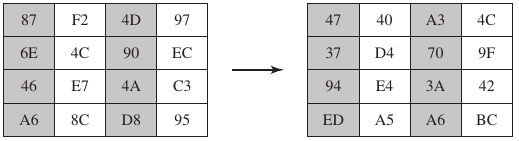
Operates on each column individually.
Mapping each byte to a new value that is a function of all four bytes in
the column.
Use of equations over finite fields to provide good mixing of bytes in
column.
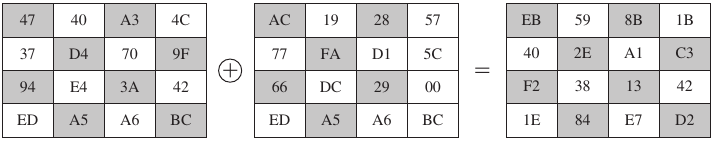
Simply XOR State with bits of expanded key (you know how to do this
now!)
Security comes from the from complexity of round key expansion and other
stages of AES
+++++++++++++++++++++
Cahoot-10a.1