Previous: 21a-OSHardening.html
https://en.wikipedia.org/wiki/Down_the_Rabbit_Hole

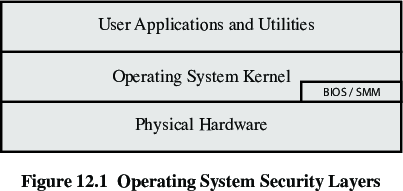
Included as part of lecture: 21a-OSHardening.html
../../DataStructuresLab/Content/00-VirtualMachines.html
https://doc.opensuse.org/documentation/leap/virtualization/html/book.virt/book.virt.html
A virtual sandbox where you can experiment with coding, hacking,
cracking, etc.
Snapshots allow reverting to earlier states!!
You can do software unit and integration testing on
other operating systems.
Security and isolation (Graders run student code in a
virtual machine for example).
Good computer hygiene (keep your OS clean).
https://en.wikipedia.org/wiki/Virtual_machine
A virtual machine (VM) is an emulation of a computer
system.
Virtual machines are based on computer architectures and provide
functionality of a physical computer.
Their implementations may involve specialized hardware, software, or a
combination.
Software simulates hardware, so that an operating system can run inside
of a software environment.
https://en.wikipedia.org/wiki/Hypervisor
A hypervisor is also known as a virtual machine
monitor (VMM).
It is computer software, firmware or hardware that creates and runs
virtual machines.
A computer on which a hypervisor runs one or more virtual machines is
called a host machine.
Each virtual machine is called a guest machine.
The hypervisor presents the guest operating systems with a virtual
operating platform,
and manages the execution of the guest operating systems.
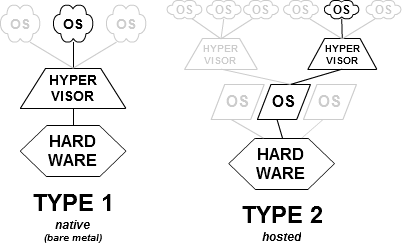
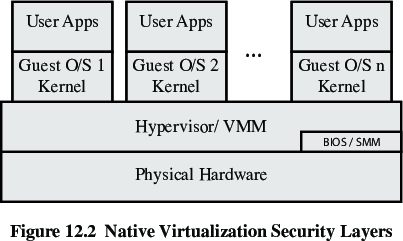
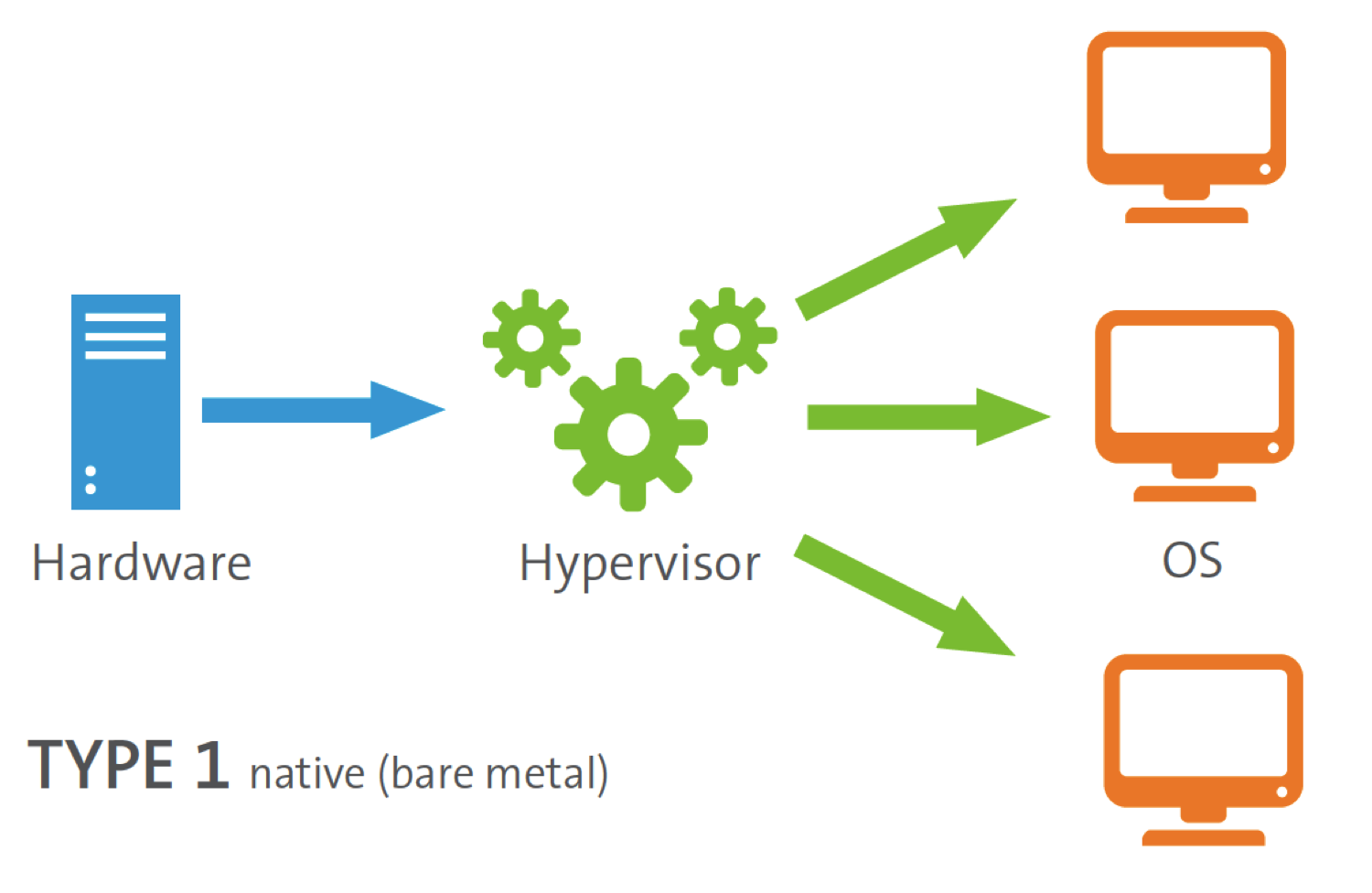
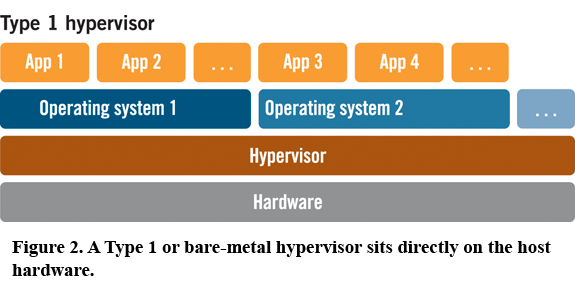
These hypervisors run directly on the host’s hardware,
to control the hardware and to manage guest operating systems.
For this reason, they are sometimes called bare metal hypervisors.
Xen is a type-1 hypervisor, for example.
These are more secure than type 2
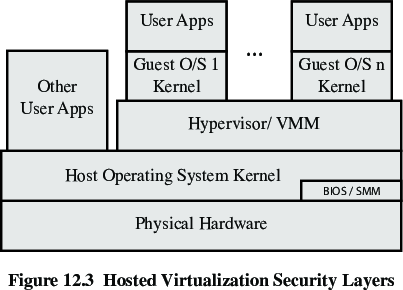
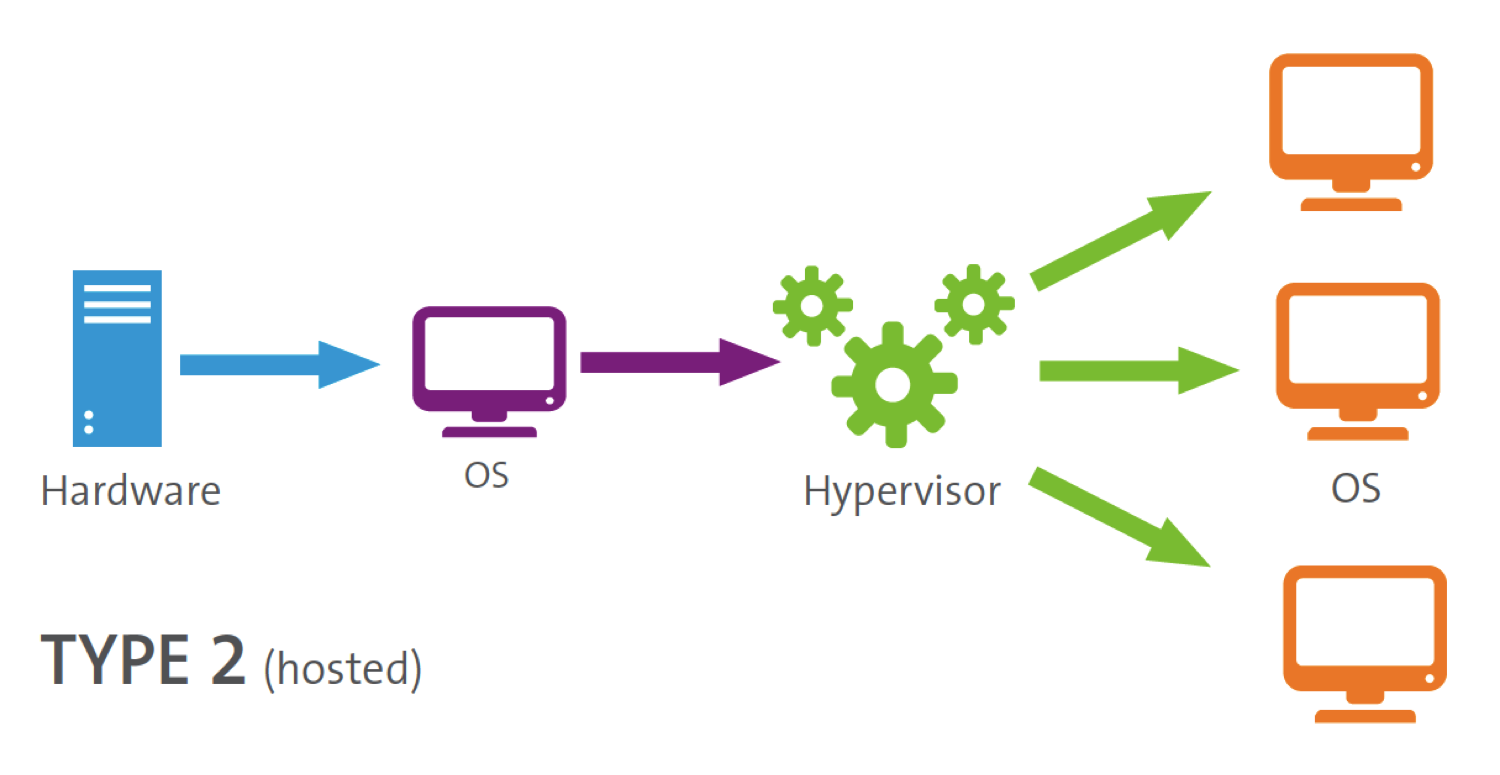
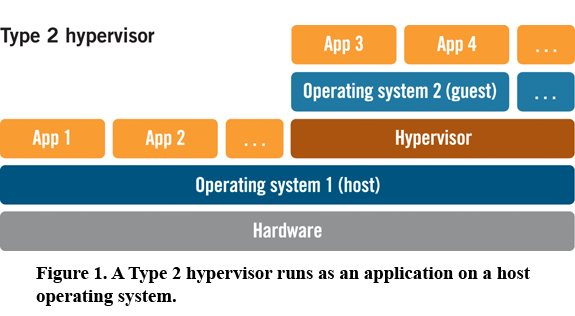
These hypervisors run on a conventional operating system (OS),
just as other computer programs do.
A guest operating system runs as a process on the host.
Type-2 hypervisors abstract guest operating systems from the host
operating system.
VirtualBox for example is a type-2 hypervisor, less secure than type
1
Still a lot better than your host alone!
Full virtualization almost complete simulation of the actual
hardware,
to allow software, which typically consists of a guest operating system,
to run unmodified.
Paravirtualization a hardware environment is not simulated
However, the guest programs are executed in their own isolated
domains,
as if they are running on a separate system.
Guest programs need to be specifically modified to run in this
environment.
https://en.wikipedia.org/wiki/Container_(virtualization)
https://en.wikipedia.org/wiki/LXC
Restricts a running process to a subset of the file system,
by mapping the processes view of root to a sub-directory of the actual
root user.
Not all processes tolerate this well,
and it can require including more directories into the jail
If a process can run as root,
then it is possible to break out of the chroot jail
One kernel allows the existence of multiple
isolated user-space instances.
Such instances, called containers, partitions,
virtualization engines (VEs) or jails (FreeBSD jail or chroot
jail),
may look like real computers from the point of view of programs running
in them.
Typical program can see all resources of that computer,
(connected devices, files and folders, network shares, CPU power,
quantifiable hardware capabilities)
but programs running inside a container can only see the container’s
contents,
and devices assigned to the container.
They can be seen as an advanced implementation of the standard chroot
mechanism,
which changes the apparent root folder for the current running process
and its children.
Kernel provides resource-management features,
to limit the impact of one container’s activities on other
containers.
Warning:
Containers like Docker are pretty easy to escape.
Use them only for minor sandboxing purposes.
https://www.virtualbox.org/
https://en.wikipedia.org/wiki/VirtualBox
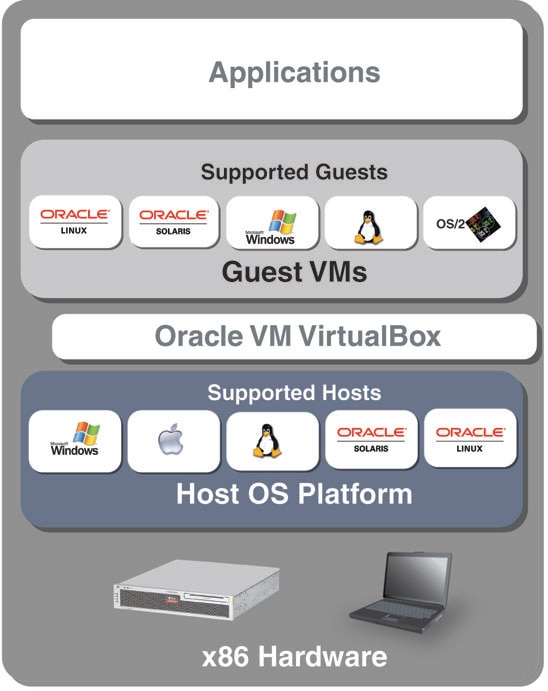
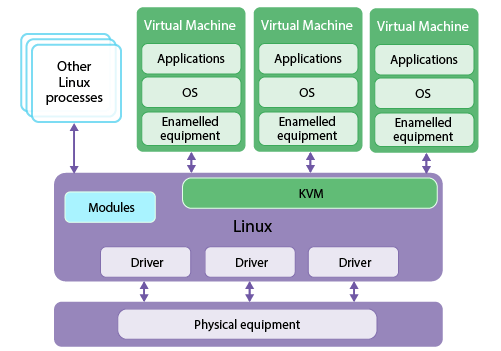
https://www.linux-kvm.org/page/Main_Page
https://en.wikipedia.org/wiki/Kernel-based_Virtual_Machine
https://doc.opensuse.org/documentation/leap/virtualization/html/book.virt/book.virt.html
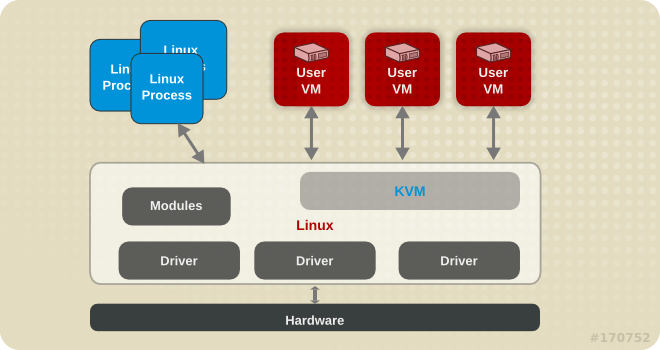
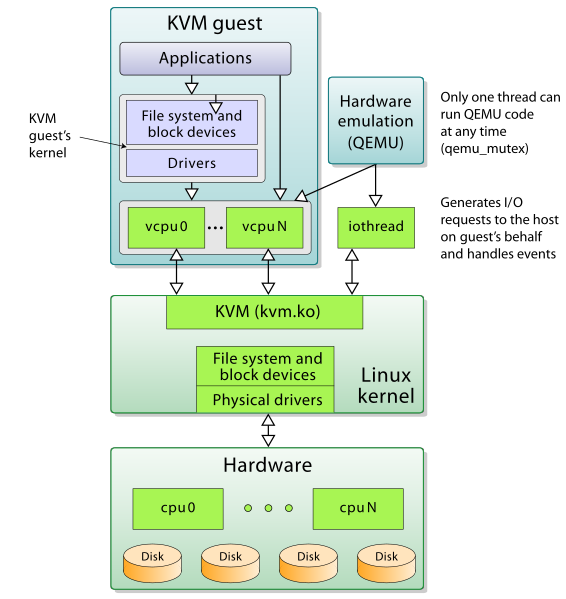
https://xenproject.org/
https://en.wikipedia.org/wiki/Xen
https://doc.opensuse.org/documentation/leap/virtualization/html/book.virt/book.virt.html
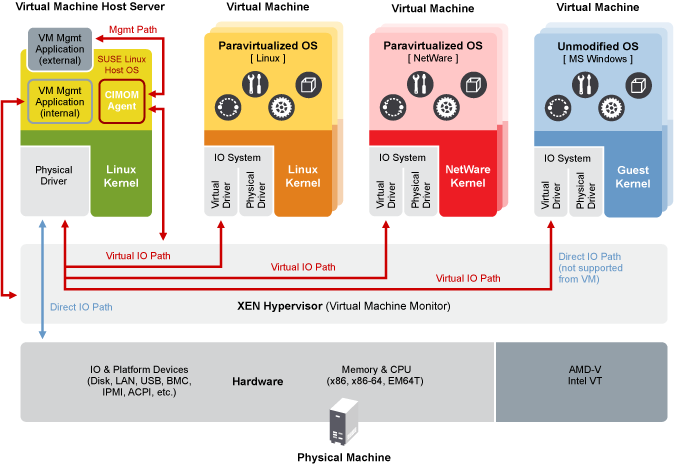
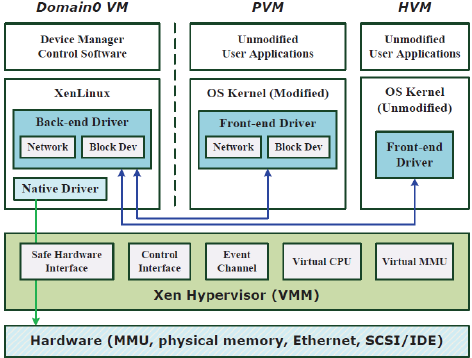
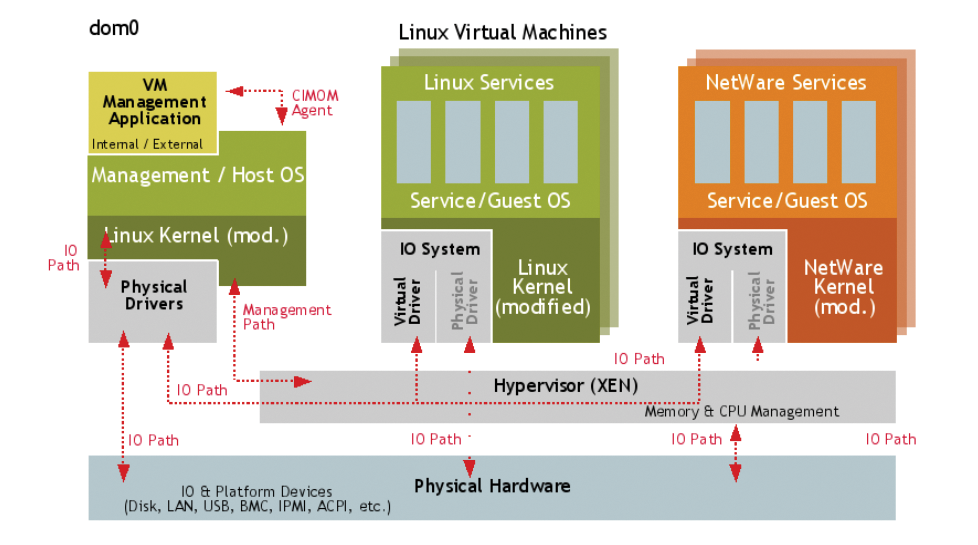
https://en.wikipedia.org/wiki/LXC
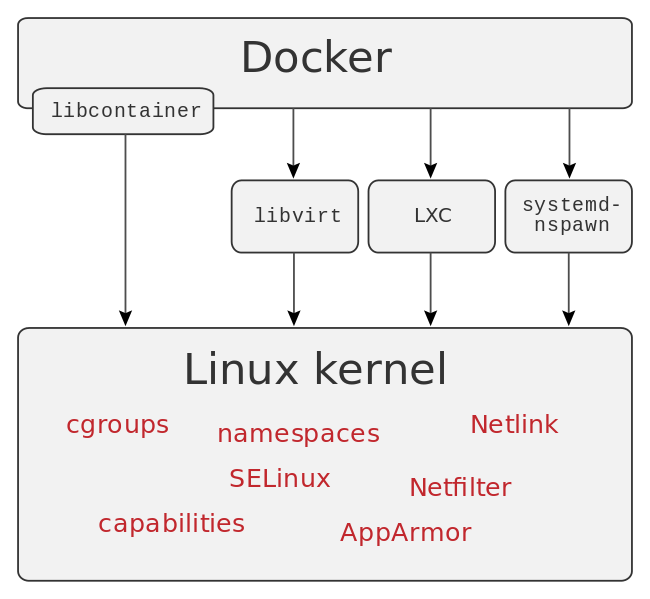
https://en.wikipedia.org/wiki/Docker_(software)
https://codereviewvideos.com/course/docker-tutorial-for-beginners
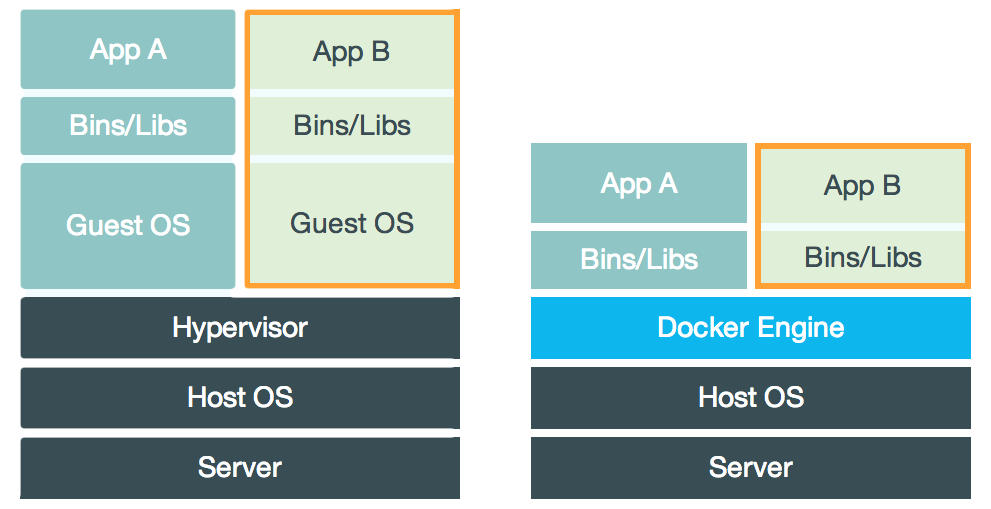
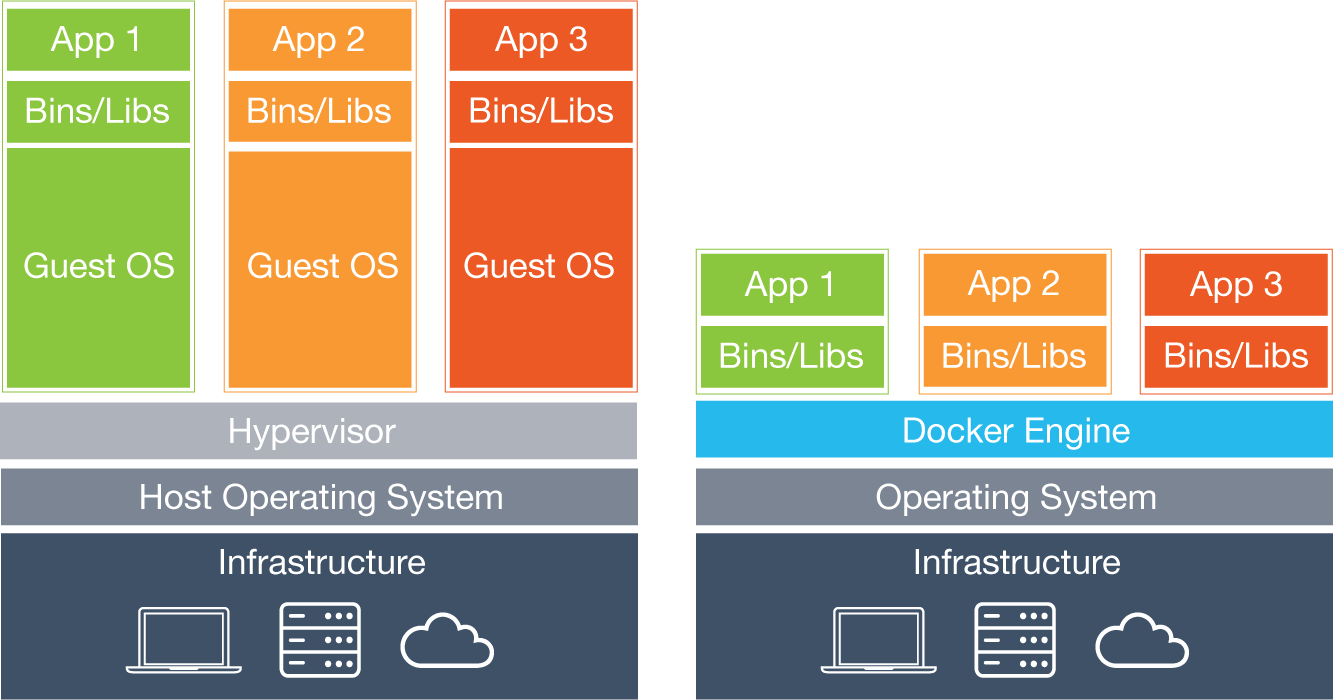
Docker vs. VM:
+++++++++++++++++++++
Cahoot-21b.1
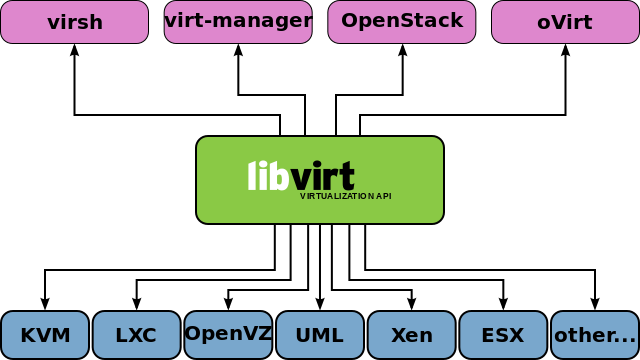
Security by isolation, in addition to security by correctness
https://github.com/bottlerocket-os
https://silverblue.fedoraproject.org/
https://fedoramagazine.org/what-is-silverblue/
A compartmentalized micro-kernel OS framework
https://genode.org/index
https://en.wikipedia.org/wiki/Genode
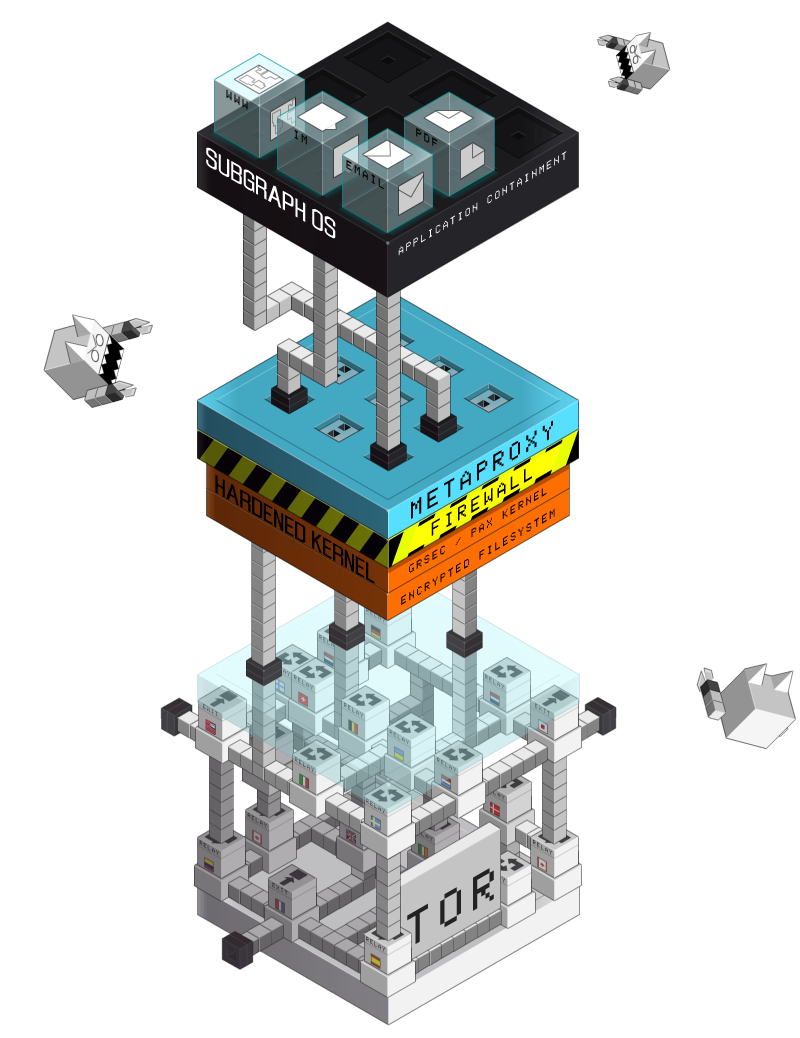
Not really a mature/stable/alive project.
Known exploits can escape containers with relative ease.
Bare metal hypervisor (Xen), with full VM for isolation.
https://www.qubes-os.org/intro/
https://www.qubes-os.org/video-tours/
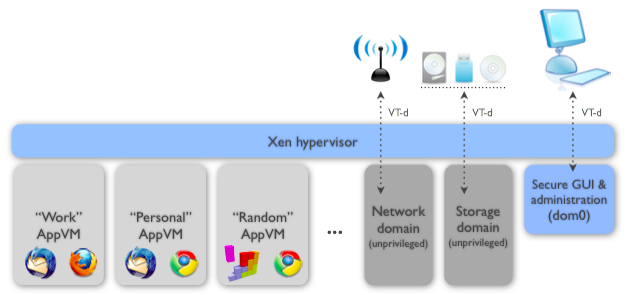
Qubes OS: detailed
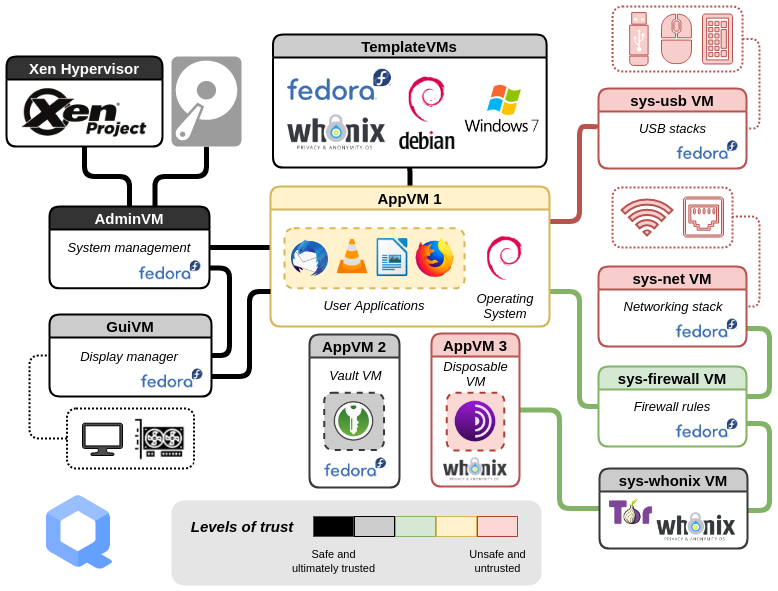
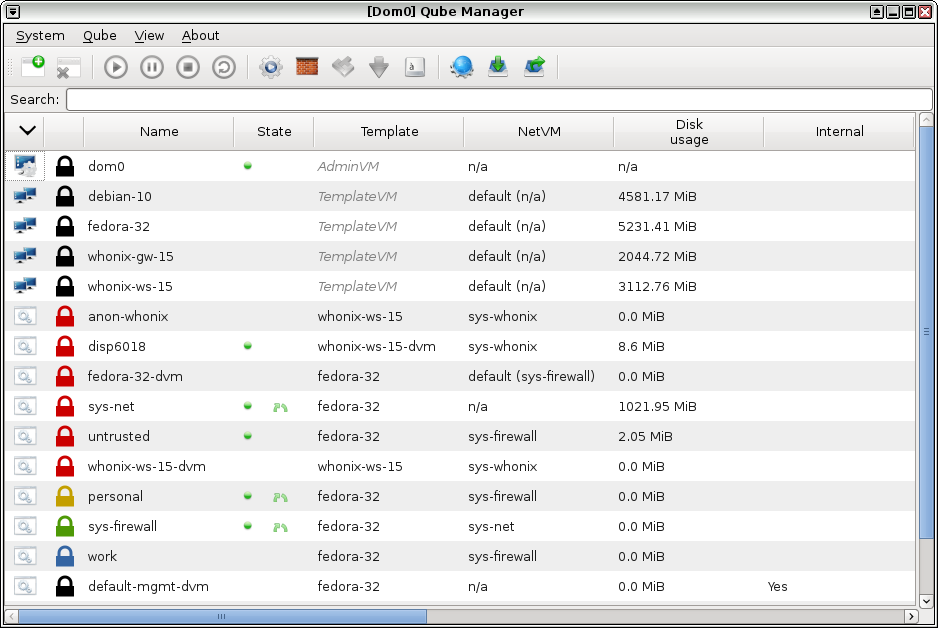
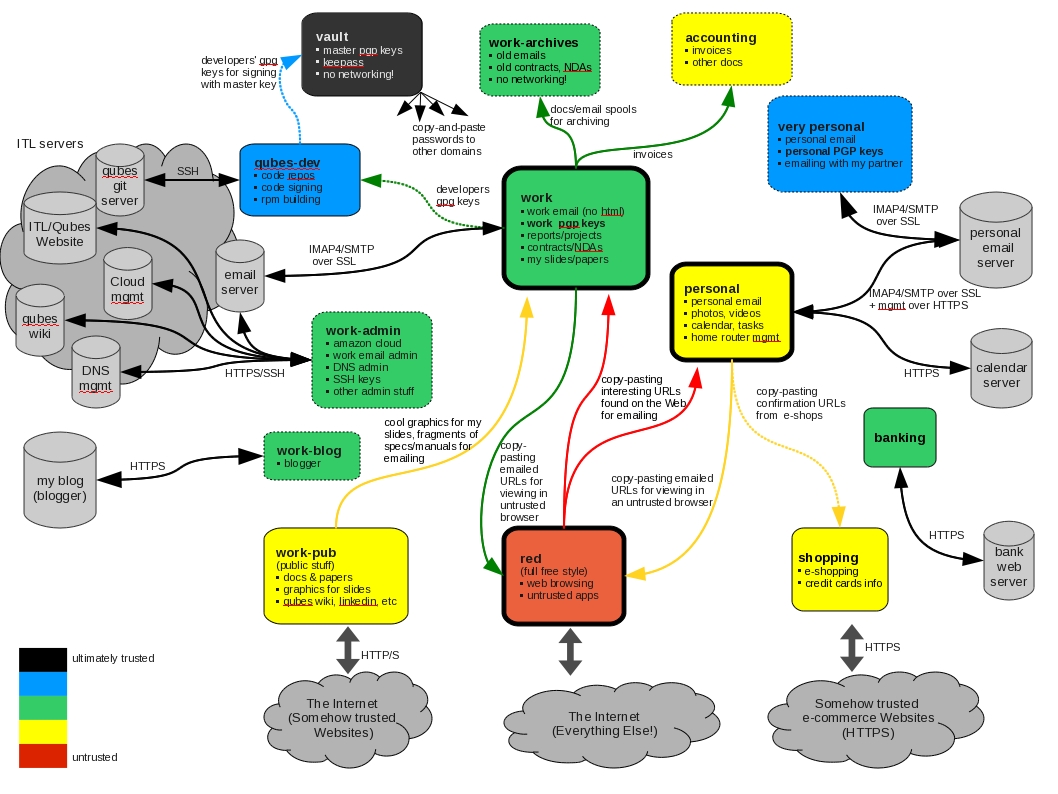
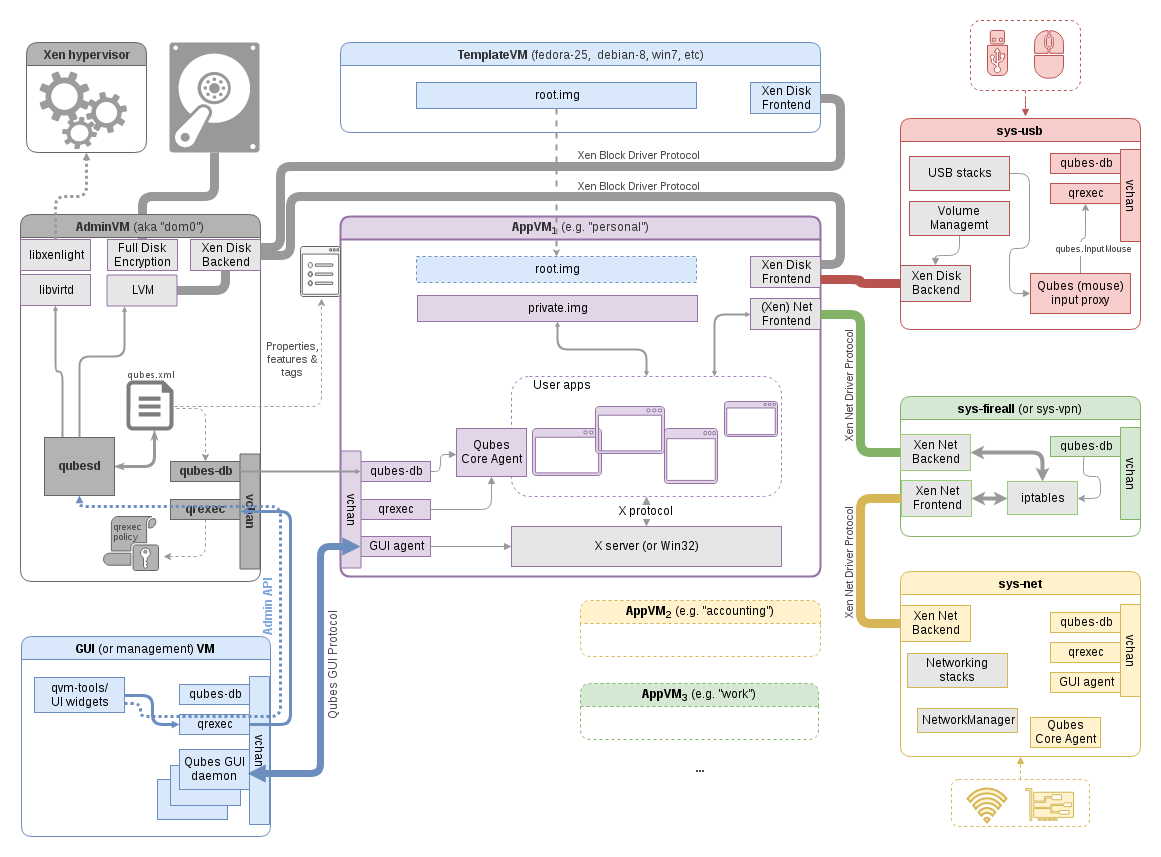
Guest OS isolation,
ensuring that programs executing within a guest OS,
may only access and use the resources allocated to it,
and not covertly interact with programs or data,
either in other guest OS’s, or in the hypervisor.
Guest OS monitoring by the hypervisor,
which has privileged access to the programs and data in each guest
OS,
and must be trusted as secure from subversion,
and compromised use of this access.
Virtualized environment security,
particularly image and snapshot management,
which attackers may attempt to view or modify.
Minimize access to the hypervisor
https://access.redhat.com/documentation/en-us/red_hat_enterprise_linux/7/html-single/virtualization_security_guide/
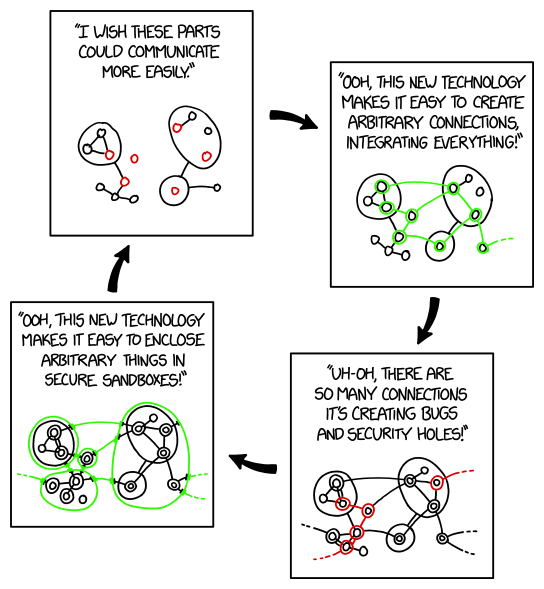
Are we going in circles here…
What about security by correctness and minimalism?
https://en.wikipedia.org/wiki/Unikernel
http://roscidus.com/blog/blog/2016/01/01/a-unikernel-firewall-for-qubesos/
A unikernel is a specialized, single address space machine
image,
constructed by using library operating systems.
A developer selects, from a modular stack, the minimal set of
libraries,
which correspond to the OS constructs required for their application to
run.
These libraries are then compiled with the application and configuration
code,
to build sealed, fixed-purpose images (unikernels),
which run directly on a hypervisor or hardware,
without an intervening OS such as Linux or Windows.
https://en.wikipedia.org/wiki/Microkernel
A microkernel is the near-minimum amount of software needed to implement
an operating system (OS).
These mechanisms include:
low-level address space management,
thread management, and
inter-process communication (IPC).
If the hardware provides multiple rings or CPU modes,
then the microkernel may be the only software executing at the most
privileged level,
which is generally referred to as supervisor or kernel mode.
Traditional operating system functions,
such as device drivers, protocol stacks and file systems,
are typically removed from the microkernel itself,
and are instead run in user space.
In terms of the source code size, microkernels are usually much smaller than monolithic kernels.
https://www.minix3.org/
https://en.wikipedia.org/wiki/Minix
The MINIX3 microkernel, for example, has approximately 12,000 lines of
code,
compared to 12,000,000 for a small monolithic kernel.
https://www.redox-os.org
https://en.wikipedia.org/wiki/Redox_(operating_system)
Inspired by those like Minix, but written in a memory safe language,
Rust.
Microkernel in Rust
https://betrusted.io/xous-book/ch00-00-introduction.html
https://github.com/betrusted-io/xous-core
Educational kernel in Rust
https://github.com/rcore-os/rCore
https://github.com/rcore-os/zCore
https://softwareengineering.stackexchange.com/questions/117973/are-there-any-os-which-are-simple-enough-for-learning
https://homepage.divms.uiowa.edu/~jones/opsys/notes/06.shtml
https://en.wikipedia.org/wiki/Network_virtualization
Network virtualization combines the functionality of network hardware
and software,
into a single, software-based administrative entity, a virtual
network.
Network virtualization involves platform virtualization,
often combined with resource virtualization.
Network virtualization is categorized as either:
external virtualization, combining many networks or parts of networks
into a virtual unit, or
internal virtualization, providing network-like functionality to
software containers on a single server.
https://blogs.oracle.com/scoter/networking-in-virtualbox-v2
https://www.virtualbox.org/manual/ch06.html
https://www.linux-kvm.org/page/Networking
https://help.ubuntu.com/community/KVM/Networking
https://jamielinux.com/docs/libvirt-networking-handbook/
https://wiki.xenproject.org/wiki/Xen_Networking
https://wiki.xenproject.org/wiki/Xen_FAQ_Networking
https://www.qubes-os.org/doc/firewall/
https://www.qubes-os.org/doc/networking/
How do you manage and build hordes of networked VMs in your virtual network?
https://www.terraform.io/
https://www.vagrantup.com/
https://www.ansible.com/
https://en.wikipedia.org/wiki/Ansible_(software)
https://en.wikipedia.org/wiki/Kubernetes
https://kubernetes.io/
+++++++++++++++++++++
Cahoot-21b.2